Penetration Testing
Recognize the risks and consequences of system vulnerabilities.
Get your ultimate guide for cloud penetration testing.
The cyber-threat landscape is constantly changing. As Cybercriminals are finding new ways to circumvent your security defenses, it is more important than ever to make sure you’re protected. Effective protection against these everchanging threats demands constant attention to stay ahead of all attackers. Performing periodic comprehensive security and penetration testing is a critical tool to identify weaknesses in your defenses before they are exploited. At PurpleBox Security we provide a personalized approach to help protect you against cyber risks, creating a plan custom fit to each client’s needs, technology, and industry.
What is Penetration Testing?
Penetration Testing (Pentesting) is an offensive security approach to test your security controls and identify weaknesses in your application, cloud, network, end-user workstations and mobile devices, and physical security controls through the eyes of a malicious actor. Our experienced security team applies the same tools and techniques used by hackers, by launching pre-authorized, controlled, and coordinated cyber-attacks on your systems. These tools and techniques are designed to gain access to sensitive information, simulate what a real-world attack would target, and demonstrate the efficiency of security controls against potential attacks and data breaches.
Types of Penetration Testing Projects
We provide a variety of security assessment and penetration testing services, ranging from external/black-box testing to full kill-chain Advanced Persistent Threat (APT) attack simulation, depending on your needs.
Network Security
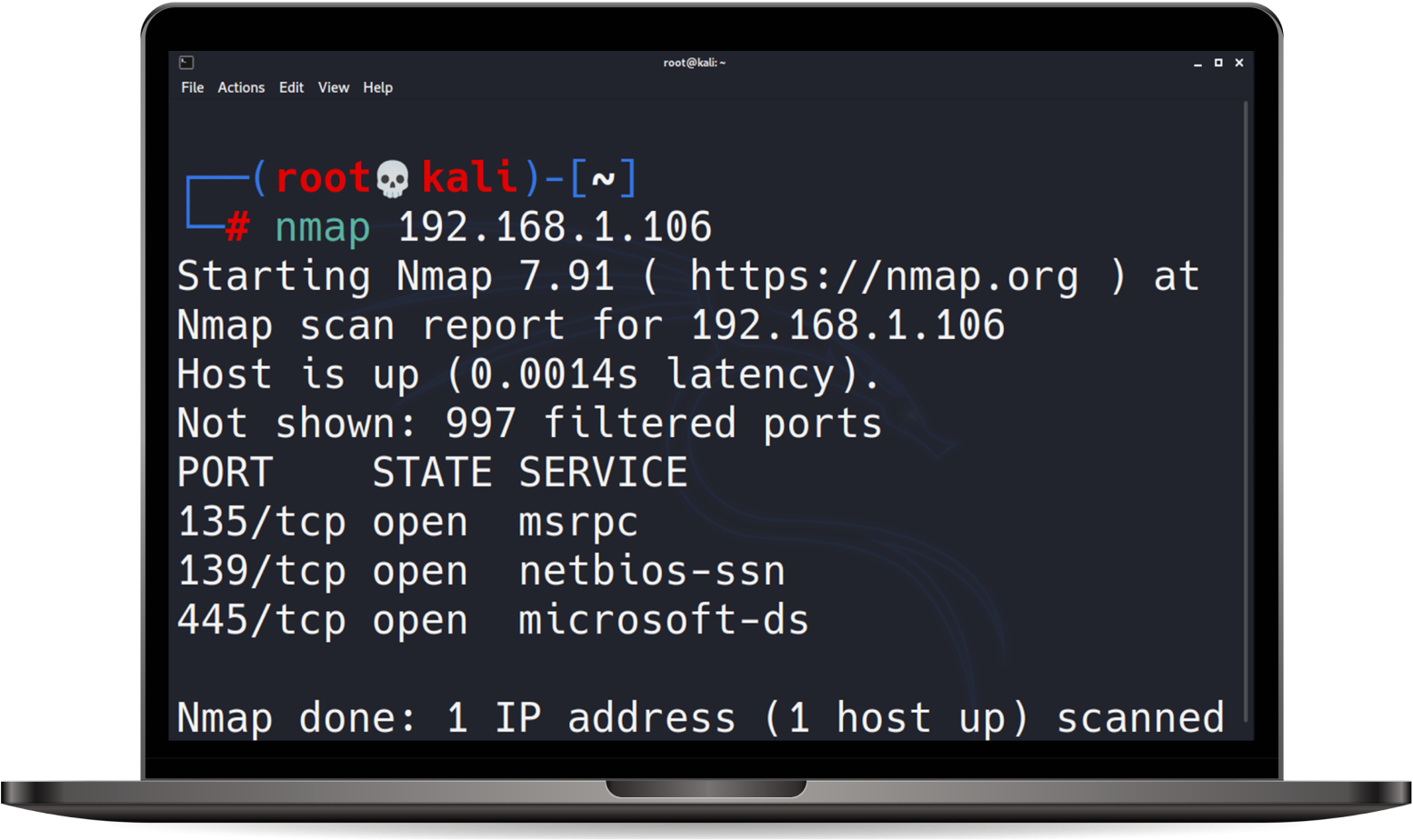
More than just vulnerability scanning, our penetration testing services also focus on assessing the security of your networks and analyze how motivated attackers can circumvent your controls by manually reviewing, testing, and exploiting issues to get to the actual risk posture, covering all aspects of your external cyber presence; networks, websites, public records, DNS, e-mail systems and certificates.
Application Security
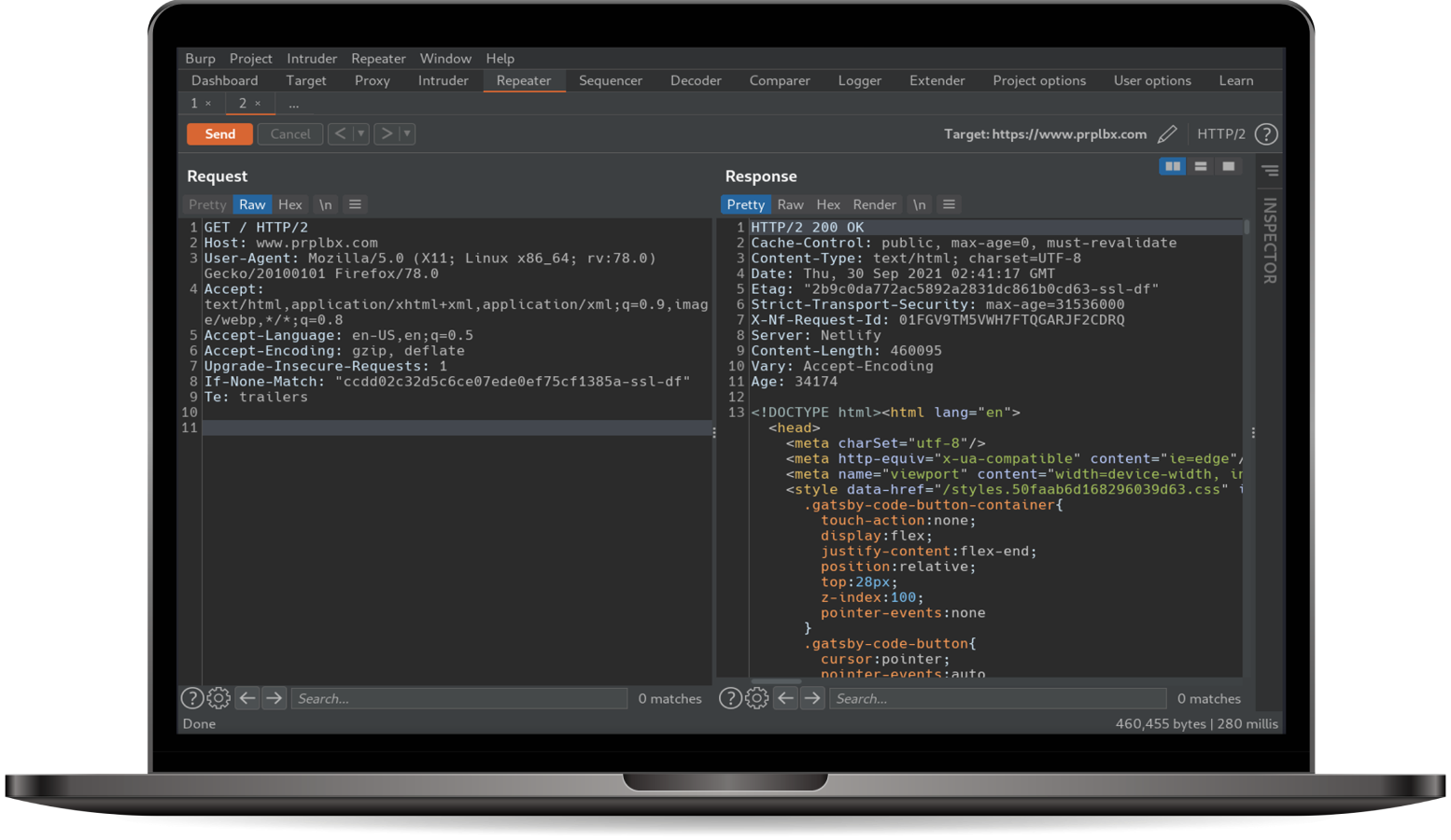
We leverage the standards and methodologies of OWASP, but go beyond just vulnerability scanning. Using commercial, open-source, and internally developed tools and research, we can find business logic faults. Application Security Pentests can cover web applications, mobile applications, APIs, source code scanning, and open-source composition analysis.
Cloud Security
It’s always critical to include cloud services such as Office365, Azure, AWS, Google Cloud (GCP), etc. in your security assessment. From public S3 buckets to exposed credentials in source code repositories, we can quickly identify risks that can result in major security incidents, leading to a resolution as soon as possible.
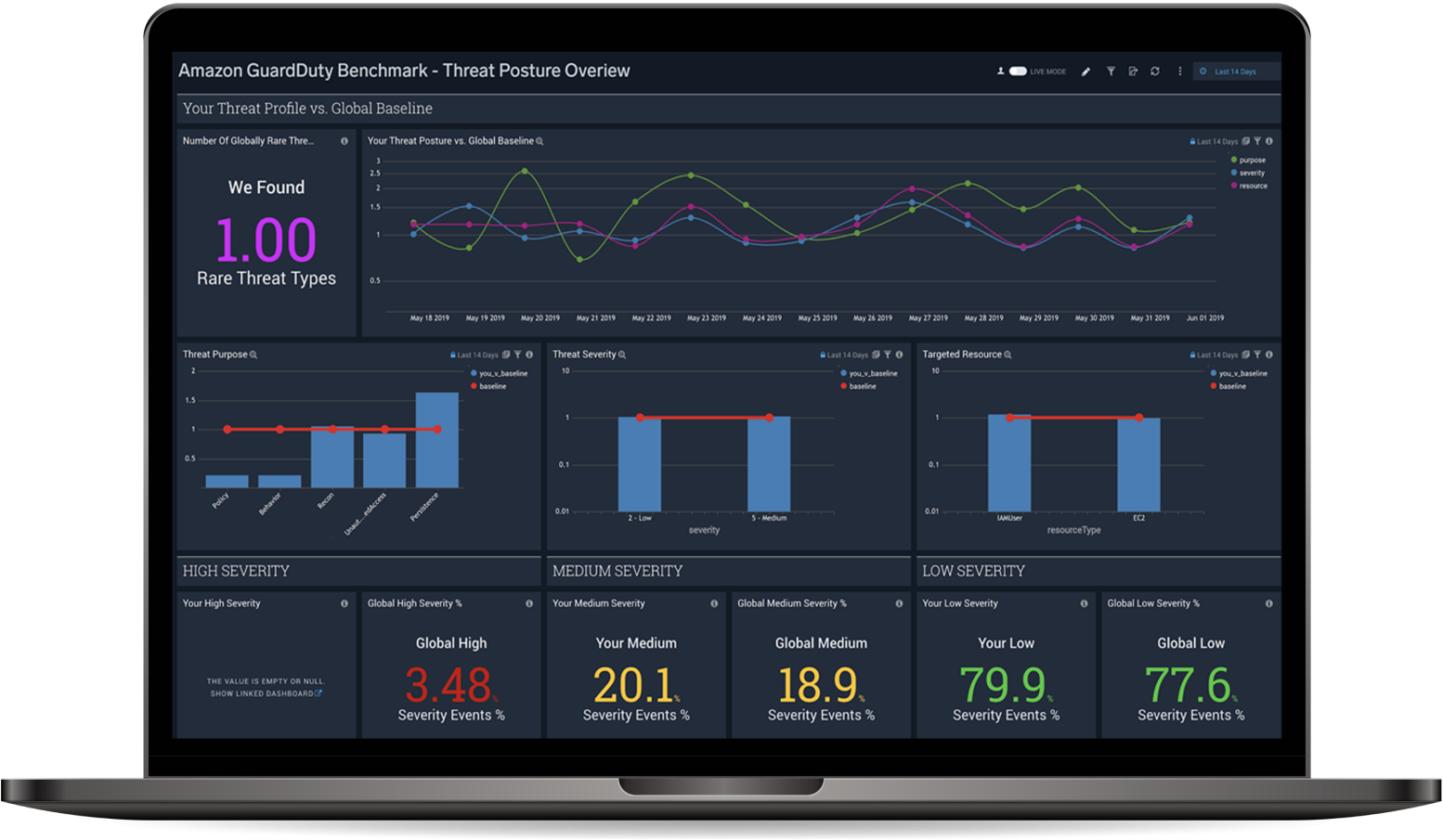
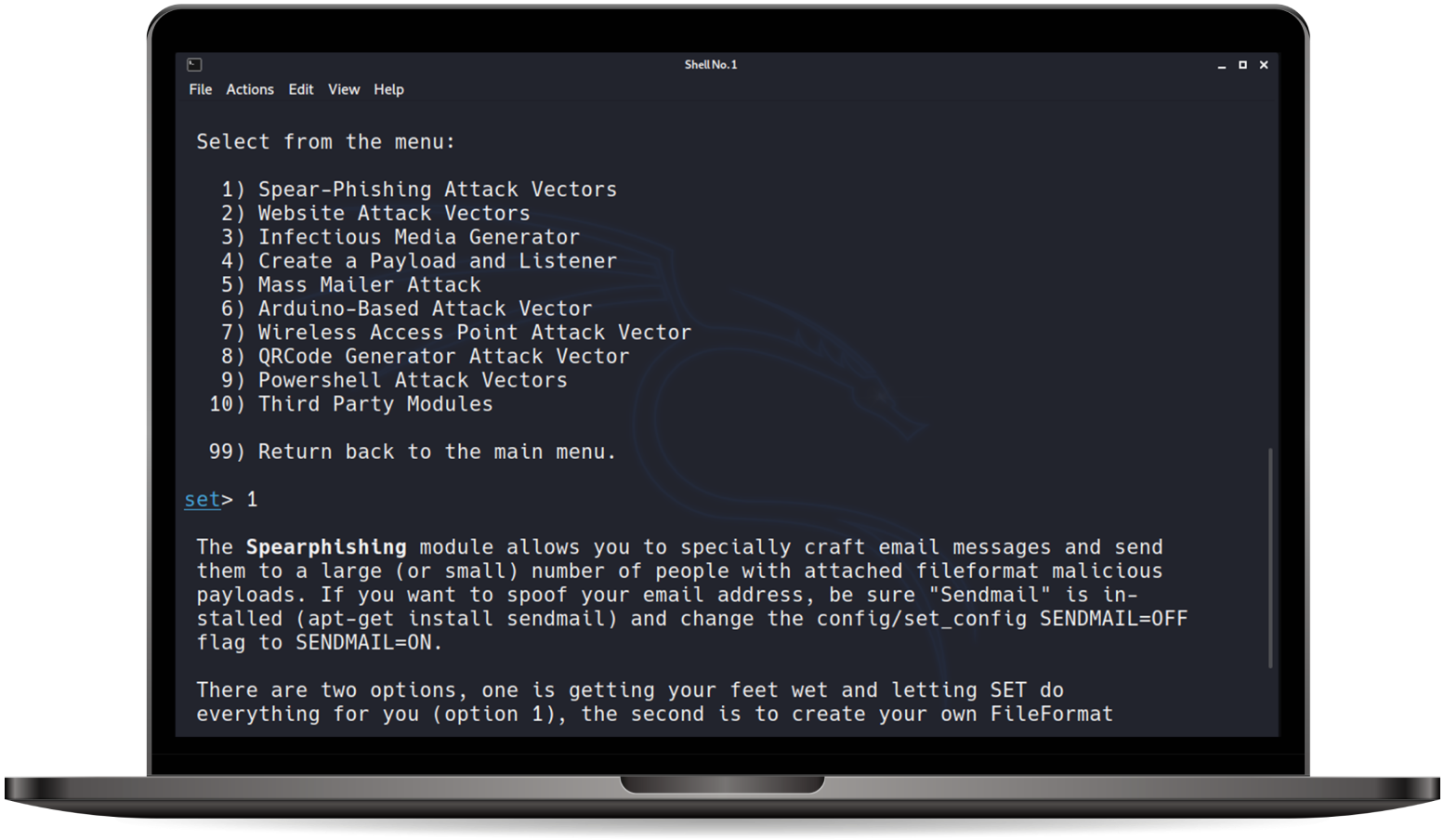
Social Engineering and Physical Security
Through a combination of advanced and proven social engineering tactics ( e.g. phishing, vishing, tailgating, pre-texting, etc.) we analyze the physical and personal aspects of your security risks, providing valuable insights on how to improve your controls while filling you in about the areas you need to focus on during your security awareness training.
Phases of a Pentest Project
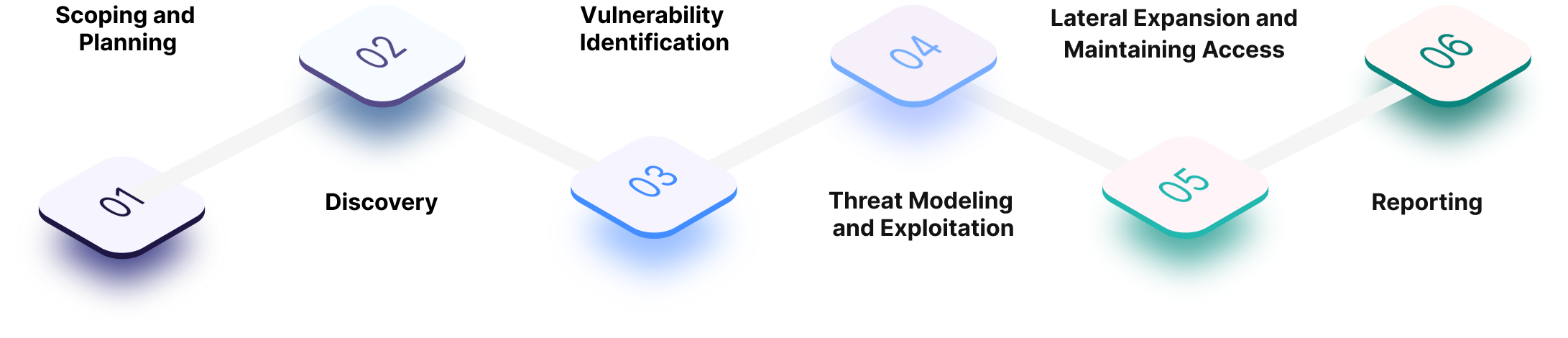
Scoping and Planning
Create a project plan with the client detailing the scope, timing, and boundaries of the project. It's critical for both the assessment team and the client to establish a clear testing window time frame so that the review does not drag on and timely remediation may be used to effectively reinforce defenses.
Discovery
Gather information on the target from public sources, including using open source intelligence (OSSINT) to find staff contact information. As much information as possible about the target, including the IP addresses, domain details, mail servers, and network topology is gathered in this stage.
Vulnerability Identification
The tester identifies targets and maps attack vectors in this phase. Using technical tools to gain further knowledge of the target's assets, including using automated scanning tools to identify networks, hosts, and vulnerabilities. The pentester will then determine whether the vulnerability can be exploited.
Threat Modelling and Exploitation
After interpreting the results from the vulnerability identification step, we then focus on developing threat models and attack scenarios to accomplish Pentest goals such as gaining remote access to systems or the customer database (e.g. using Metasploit to run exploits against known vulnerabilities).
Lateral Expansion
After gaining access, we then test lateral expansion to simulate how far an attacker can go and whether your security monitoring controls would detect their activities. The pentester must perform cleanup of the organization, removing any components they have added to the environment as well as access or privileges they received.
Reporting
Provide executive management and technical reports that include business risks, technical vulnerabilities, as well as suggested remediation strategies. Additionally, the comprehensive report will also cover the security testing and discovery of vulnerabilities in addition to the way they were exploited.
Benefits of Penetration Testing
Identify exposure to external attacks
Test the strength of your security defense and your organization's ability to successfully detect, respond to, and put a stop to an attack. Protect your organization from external attacks and data breaches before they happen.
Gain a holistic & accurate view of risk
Assess the potential business, operational, and regulatory impact of successful cyberattacks. Establish a strategic risk management program built on a security framework to gain comprehensive insights into your operating environment.
Professional Risk Management
Guide decision-makers for security investments based on the effectiveness of existing controls, as well as areas that need improvement. A penetration test will reveal a comprehensive list of vulnerabilities in the target environment as well as the potential risks that come with them.
Comply with regulations and standards
Meet compliance with regulatory requirements and industry standards such as ISO2700, PCI- DSS, FISMA, NIST, HIPA, etc. These regulations and standards require system owners to conduct regular security reviews and penetration tests by qualified testers.
Protect clients, partners, and third parties
A security breach can affect clients, partners, and third-party contractors. It will help professionals build trust and confidence within the organization if the company ensures protection for these parties through penetration testing.
Prevent financial losses
Provide executive management and technical reports that include business risks, technical vulnerabilities, as well as suggested remediation strategies. Additionally, the comprehensive report will also cover the security testing and discovery of vulnerabilities in addition to the way they were exploited.
Why PurpleBox Security?
PurpleBox Security specializes in Security assessment and Pentesting services. We place a high value on testing important devices and components. Our comprehensive reports are produced by experienced, skilled testers so that the actionable information contained within them is easily understood. Combining our Red Team (Offensive) capabilities with our Blue Team (Defensive) experience, we provide a unique approach to solving enterprise security problems.
Download The Guide
Download the Ultimate Guide for Cloud Penetration Testing to learn more about the benefits, tools, challenges, and threats.
Unraveling Kubernetes Security: A Comprehensive Pentesting Guide
January 10, 2024
Linux Privilege Escalation with PATH Variable & SUID Bit
January 17, 2023
Overcome Your SecurityChallenges
We offer 360° Security protection for your business with our trusted experts in cybersecurity.