Ransomware attacks can cause massive disruptions to a business’s productivity, resulting in loss of critical files and demands for payment. To prevent such threats and improve your IT security posture, implement EDR solutions. EDR blocks ransomware attacks before they can hurt your organization, and any encrypted files are rolled back to a secure state. This allows your workforce to continue working uninterrupted with minimal disruption to your business.
After cleanup, you’ll receive full post-cleanup information, providing a comprehensive timeline of the attack and helping you identify the entry point and what was affected. With EDR, you can protect your business from ransomware attacks and ensure your critical files are secure.
What is Endpoint Security?
Endpoint security combines preventative protection with a new breed of continuous detection and response capabilities. Using cloud-based analytics, it eliminates bloated agents from consuming valuable CPU resources so employees can get their work done and businesses remain protected.
Endpoint protection systems are designed to quickly detect, analyze, block, and contain attacks in progress. To do this, they need to collaborate with each other, and with other security technologies, to give administrators visibility into advanced threats to speed detection and remediation response times.
Types of Endpoint Security Services
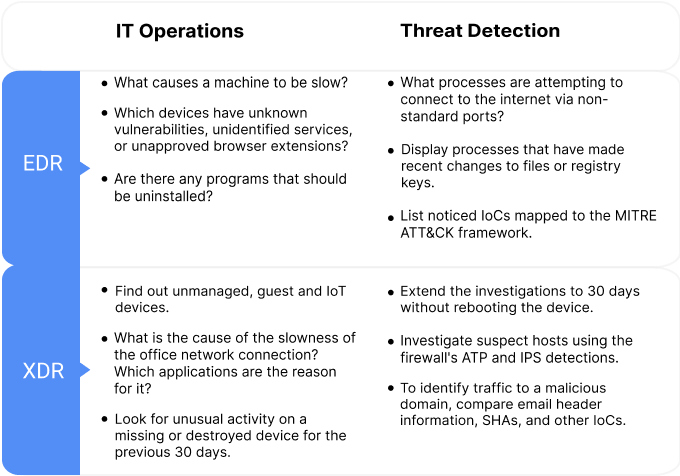
Endpoint Detection and Response (EDR)
Endpoint detection and response (EDR) tools are designed to increase and improve detection, investigation, and response capabilities for endpoint security.
EDR provides information about what has occurred in the past and what is currently occurring on the endpoints. Threats can be tracked to detect active attackers and IT operations can be leveraged to maintain strong and effective IT security hygiene. When a problem is discovered remotely, i̇t enables a corresponding rapi̇d response to limit the damage.
EDR prevents breaches from occurring by starting with the strongest protection possible. When hunting down threats and strengthening your IT security operations posture, EDR gives you valuable tools to ask detailed questions and improve your security standing.
Extended Detection and Response (XDR)
XDR integrates firewall, email, network, email, cloud, mobile and other data sources in addition to endpoints and servers. It provides a comprehensive picture of your company’s cybersecurity posture, with the option to drill down into granular detail if necessary.
Using XDR, you can swiftly identify, isolate, and eliminate a threat by comparing attack indicators from numerous data sources. XDR allows you to locate unmanaged, guest, and IoT devices throughout your organization’s network. It also enables you to identify any office network problems, as well as the applications that are causing them.
Managed Threat Response
Managed Threat Response (MTR) facilitates threat hunting through the use of proactive 24/7 tracking by our threat analysts, making the potential impact and context of threats to your business visible to you at any time.
MTR Initiates actions to remotely disrupt, contain, and neutralize threats on your behalf to stop even the most sophisticated threats. It empowers continuous Improvement by addressing the root cause of recurring incidents to stop them from occurring again, rather than simply one-time fixes.
Maintain IT Security by Threat Hunting
Maintain IT Security by Threat Hunting
Keep up with IT security efforts. cleanliness, and track out malicious threats. Answer business-critical IT operations and threat hunting questions.
Add Expertise Not Employees
Suspicious activity investigations can be difficult and time-consuming. We have the expertise to assist you to answer questions about security.
Maintain the Strongest Protection
Gain access to threat intelligence and stop data breaches before they start by consolidating EDR with the best security practices.
Top 6 Reasons Why You Need EDR
1. Maintain IT security operations
EDR enables admins the ability to remotely access devices to investigate performance issues, apply patches, and disable RDP and guest accounts. EDR tools detect subtle, complex threats and automatically track down any indicators of compromise (IoCs).
2. Detect undiscovered attacks
Organizations frequently rely solely on prevention to stay safe, but EDR has the potential to uncover incidents that have gone unnoticed. EDR assists in locating all instances of any suspicious items throughout the entire estate, taking quick action to address these issues and prevent future attacks.
3. Respond quickly to new vulnerabilities
Stopping an attack from spreading is the first step security analysts take throughout the incident response process. Security and IT professionals typically spend more than three hours trying to resolve each issue, making response slow and inefficient. This can be considerably accelerated with the help of EDR, significantly cutting down on response time and improving efficiency.
4. Provide expertise with minimum headcount
Organizations wishing to implement endpoint detection and response capabilities rate “staff knowledge” as the most significant hurdle to EDR adoption. Machine learning can be used to combine deep security understanding and threat intelligence, making EDR adoption a much faster and more efficient process.
5. Prevent attacks from happening again
Identifying and removing malicious files solves the immediate problem, but it doesn’t reveal how the files got there or what happened before the attack was stopped. This information is essential in understanding security vulnerabilities and improving your cybersecurity standing. EDR helps the IT team to prevent an attack from happening again if they understand the fundamental cause.
6. Enhanced data monitoring and management
EDR solutions are built in such a way that they can collect and monitor data from all of the network’s endpoints. They constantly gather and monitor information about potential network cybersecurity threats. This information allows you to adjust to new attack strategies as attackers gradually become smarter and thus more dangerous. On endpoints, data is collected and stored in the form of a database.
Benefits of EDR
Begin with the most effective protection
Experience greater security, 24/7 access to detailed threat intelligence, and automated threat intelligence research, giving you more time to focus on business operations.
Start operating right away
Choose from a vast library of pre-written SQL queries to ask a wide range of IT and security inquiries. Customize or create new queries based on your needs.
Answer threat hunting questions
Get quick, detailed answers to business-critical questions when executing day-to-day IT operations and threat hunting duties.
Investigate information and act quickly
Pivot and deep dive to acquire rich details live. Get immediate access to a comprehensive, detailed report of any potential threats.
Boost the ROI of security investments
Correlate data across endpoint, network, and cloud security tools to deliver excellent holistic security and avoid missing any important alerts in the clutter.
Get information at all times
Store and access critical information from your endpoints, servers, firewall, and email, even when devices are offline.
Why PurpleBox Security?
PurpleBox Security specializes in Security assessment and Pentesting services. We place a high value on testing important devices and components. Our comprehensive reports are produced by experienced, skilled testers so that the actionable information contained within them is easily understood. Combining our Red Team (Offensive) capabilities with our Blue Team (Defensive) experience, we provide a unique approach to solving enterprise security problems.
Unraveling Kubernetes Security: A Comprehensive Pentesting Guide
January 10, 2024
What is Red Teaming?
February 2, 2023
Overcome Your SecurityChallenges
We offer 360° Security protection for your business with our trusted experts in cybersecurity.