Keeping your business compliant and secure in the cloud requires more than standard technologies. An enterprise-grade cloud security framework will grow with your company while using cutting-edge machine learning capabilities to detect threats before they become problems for your business. Use our security automation services to help protect your critical data & enable continuous compliance without disrupting business.
At PurpleBox, our certified cloud security experts evaluate your current systems and develop a comprehensive cloud security plan tailored to your specific needs. We configure cloud environments like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) while protecting sensitive regulated data in the cloud. With trusted partners and optimal technology, we ensure a smooth cloud transformation process.

What is Cloud Security?
“Cloud security” refers to the practices, technologies, and policies that help protect cloud-based systems, data, and infrastructure from unauthorized access, data breaches, and other threats. It involves implementing security measures such as access controls, data encryption, and network security to safeguard cloud environments. Cloud security is becoming increasingly important as more businesses move their operations to the cloud, and it requires specialized expertise to ensure that cloud-based systems and data are adequately protected.
Cloud Security Assessment
Our cloud security team assess your posture by identifying issues and vulnerabilities in your assets and resources. This includes misconfigurations, unwarranted access, and non-standard deployments. Our automated monitoring follows industry standards and regulatory mandates to prevent security issues such as leaky storage buckets, unrestricted security groups, and crypto-mining attacks in major cloud providers like AWS, Azure, and Google. Our recommendations for improvement are based on proven cloud practices and CIS benchmarks.

Securing Delivery Pipelines
To stay up-to-date with modern IT practices, you need to continuously integrate, deliver, and deploy your software development and testing processes. PurpleBox helps you achieve this by integrating automatic security checks into your pipeline, providing you with early alerts and ongoing monitoring for any security flaws. As your company expands, utilizing PurpleBox’s integrated continuous security techniques becomes increasingly important, allowing you to keep your cybersecurity up-to-date at all times.
DevSecOps Maturity Assessment
DevSecOps is a set of processes and technologies that assist cloud teams in enhancing the pace and efficiency of their security efforts. When DevOps principles are applied to software security, security testing becomes an active, fully-integrated part of the development process. We’ll take your security controls and turn them into architectural solutions based on AWS, utilizing several useful features the cloud has to offer.
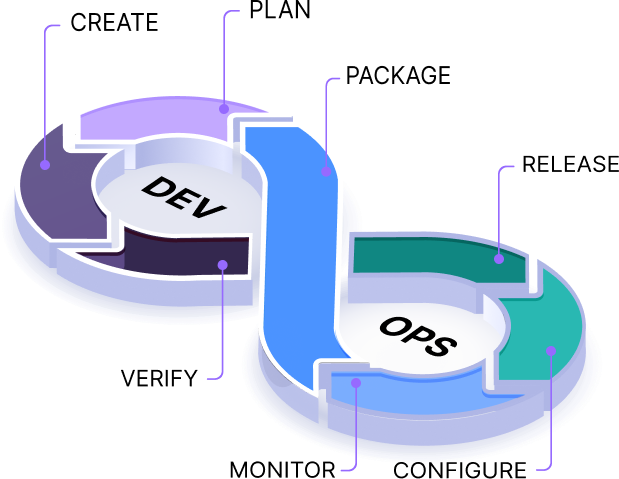
Container Security Strategy
We assess your containerized environments, detect your misconfigurations, and scan your container images, hosts, and container during runtime. Our comprehensive reports are integrated with your DevOps and CI/CD processes to identify and minimize any container security risks.

DevSecOps Consulting
DevSecOps transforms traditional security engagement into an active process integrated into the software development life cycle (SDLC). Our Managed Cloud Services incorporate DevSecOps best practices, including active testing and code verification during agile development. Our certified engineering team can manage your AWS, Azure, and GCP infrastructure while implementing these best practices.
Additionally, we provide security consulting services for data protection, disaster recovery, and assist your DevOps and in-house security teams in developing your entire cloud security requirements.

Raise your security posture
Secure your sensitive data and maintain compliance with ease using security automation. By utilizing the most flexible and secure cloud computing environment available, you can confidently run your business while gaining complete control. Automated security tasks can help reduce human error, freeing up your time to focus on scaling and innovating your business. Start experiencing the benefits of security automation today.
Protect your data
For a seamless adoption strategy, define user rights and identities, infrastructure protection, and data protection procedures.
Respond Automatically
Automated incident response and recovery to assist security teams in shifting their major focus from response to root cause analysis.
Remediate by Using Automation
Use event-driven automation to swiftly remediate and secure your cloud environment.
Identify business security solutions
Explore your company’s security posture by logging and monitoring services.
Benefits of Cloud Security
Scale with improved visibility
Detect unusual security events throughout your ecosystem using our security automation and activity monitoring services to reduce risk as you expand.
Design with security standards
Build upon the most secure infrastructure in the world, knowing that you can encrypt, transfer data, and manage retention. Because of the way our global infrastructure is built, you have complete control over where your data is physically stored, helping you to satisfy data residency rules.
Deeply Integrated Services
Choose from a selection of tightly connected solutions that may be used to automate activities in new ways, allowing your security team to collaborate more closely with developers and operations teams to deliver code quicker and more securely.
Productivity with a secure ecosystem
In a matter of minutes, locate, purchase, implement, and manage cloud-ready software solutions that inclue software as a service package. These solutions work together to help protect your data in ways that aren't feasible on-premises.
Take advantage of security
Experience third-party validation for thousands of worldwide compliance criteria that are continuously monitored. Gain access to up-to-date security controls and several useful tools designed to help minimize the cost and time spent on security. Start experiencing the benefits of bolstering your compliance with up-to-date security controls today.
High availability and support
A best-practices cloud computing security solution ensures that a company's assets are always protected. This includes live monitoring every day of the year, 24/7. There are also several built-in redundancies to ensure that your company's website and applications are always up and running.
Why PurpleBox Security?
PurpleBox Security specializes in Security assessment and Pentesting services. We place a high value on testing important devices and components. Our comprehensive reports are produced by experienced, skilled testers so that the actionable information contained within them is easily understood. Combining our Red Team (Offensive) capabilities with our Blue Team (Defensive) experience, we provide a unique approach to solving enterprise security problems.
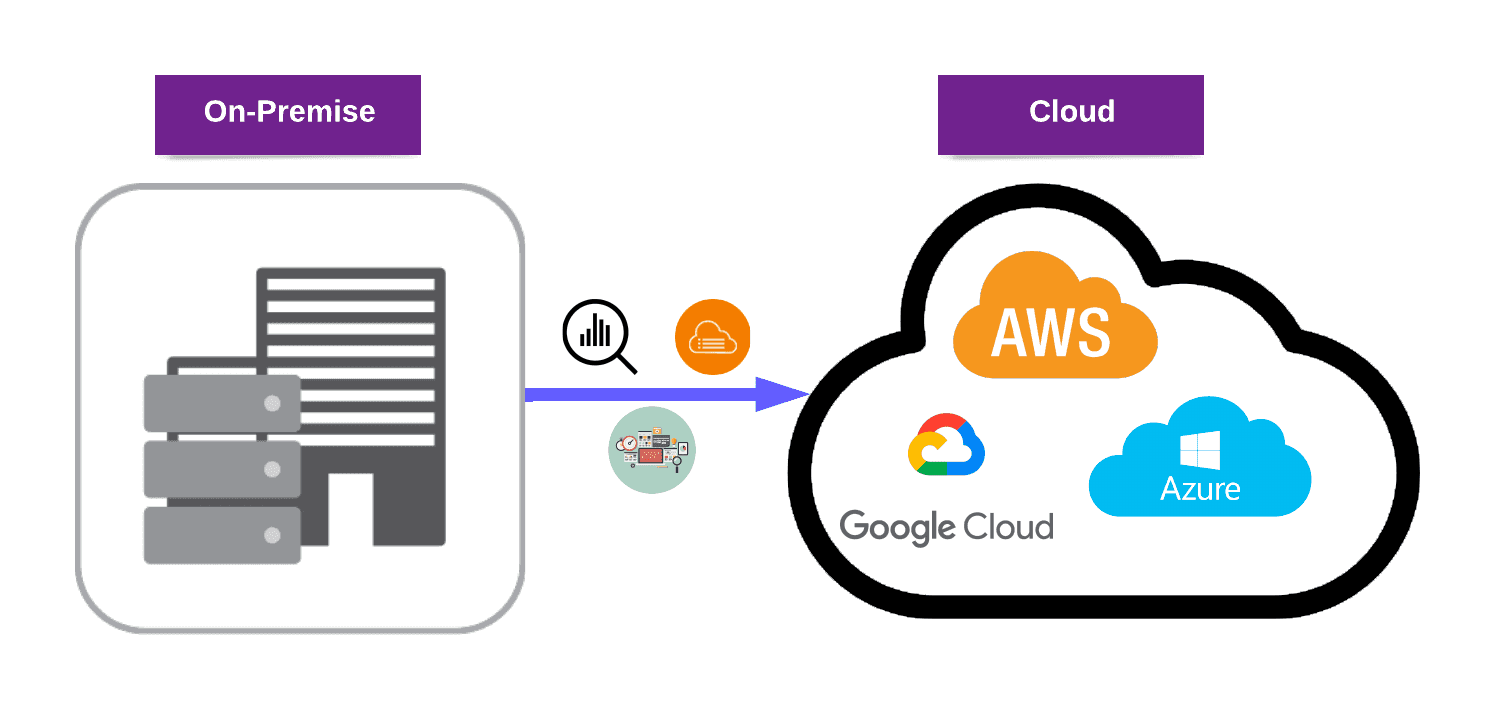
The Ultimate Guide for Cloud Migration
April 16, 2023
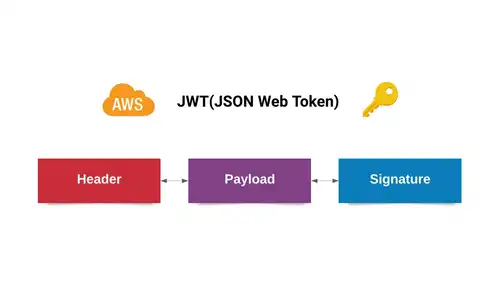
Custom JWT Generation for Cloud Solutions
January 5, 2023
The Ultimate Guide for Cloud Penetration Testing
November 17, 2022
Overcome Your SecurityChallenges
We offer 360° Security protection for your business with our trusted experts in cybersecurity.