February 2, 2023
What is Red Teaming?
December 15, 2022
What is a Web Application Firewall?
December 8, 2022
The Ultimate Guide for Broken Authentication
November 17, 2022
The Ultimate Guide for Cloud Penetration Testing
November 10, 2022
A Complete Guide To Server-Side Request Forgery (SSRF)
July 20, 2022
Methods For Exploiting File Upload Vulnerabilities
March 16, 2022
What is a Cyber Attack?
January 19, 2022
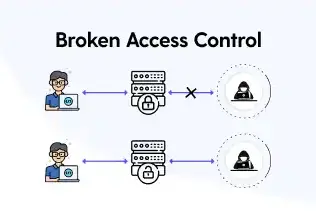
Broken Access Control vs Broken Authentication
December 17, 2021
What is Apache Log4J Vulnerability and How to Prevent It?
October 13, 2021
Welcome SSRF! Take a Look at the New Member of OWASP Top 10!
August 18, 2021