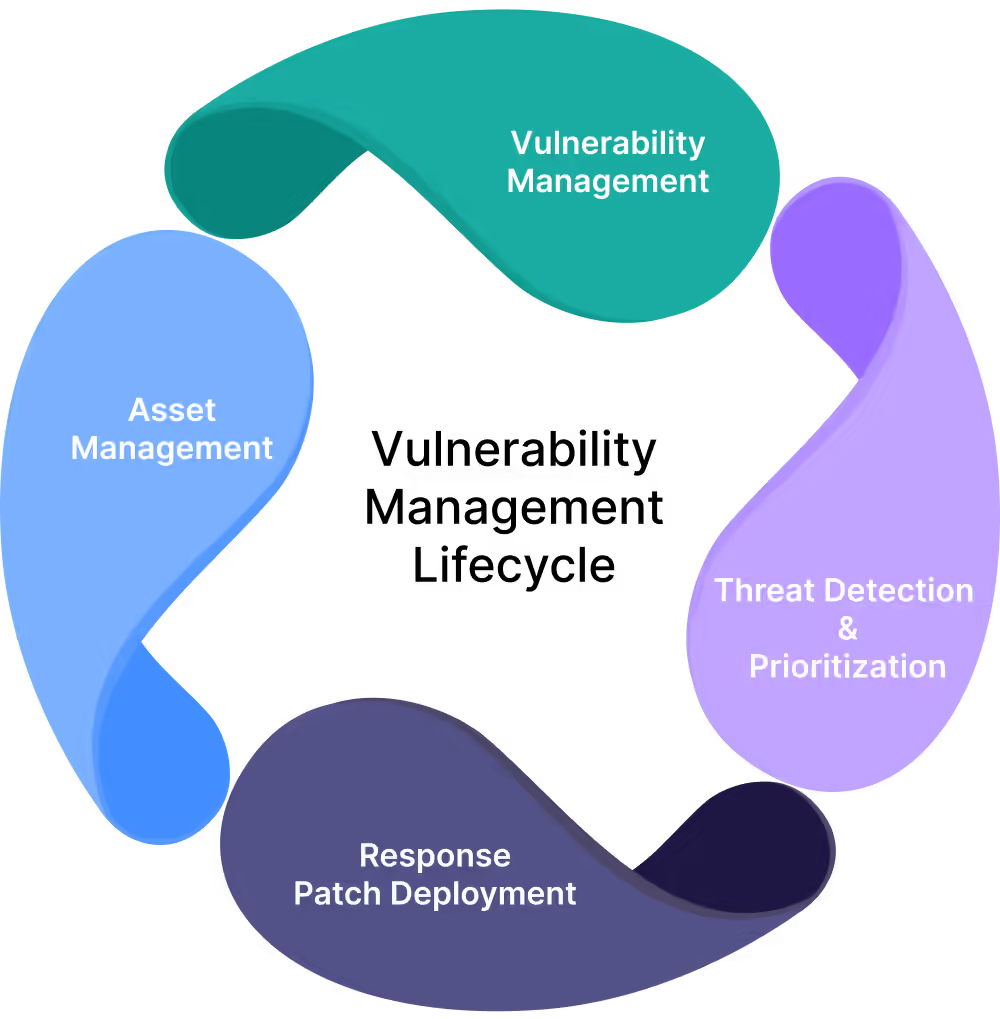
Vulnerability Management
Detect and Defend Against Threats in Real-Time Anywhere and Everywhere
Businesses use the Internet to connect employees, suppliers, and customers globally. However, connecting to the Web poses security risks. Cybercriminals can exploit vulnerabilities to hack networks, steal confidential information, and abuse IT resources. Within an hour of connecting to the Internet, attackers start exploring for vulnerabilities, and if left unsecured, they can launch devastating attacks within 24 hours. Adopting a Vulnerability Management (VM) solution can prevent most attacks. VM enables continuous monitoring of network infrastructure and staying ahead of criminals to safeguard corporate resources.
What is Vulnerability Management?
Vulnerability Management involves monitoring, detecting, assessing, reporting, managing, and resolving security vulnerabilities across endpoints, workloads, and systems. Security teams use vulnerability management tools to detect vulnerabilities, and different processes to patch or fix them. Strong vulnerability management programs use threat intelligence and comprehensive knowledge of IT and business operations to prioritize risks and address vulnerabilities promptly, preventing devastating attacks.
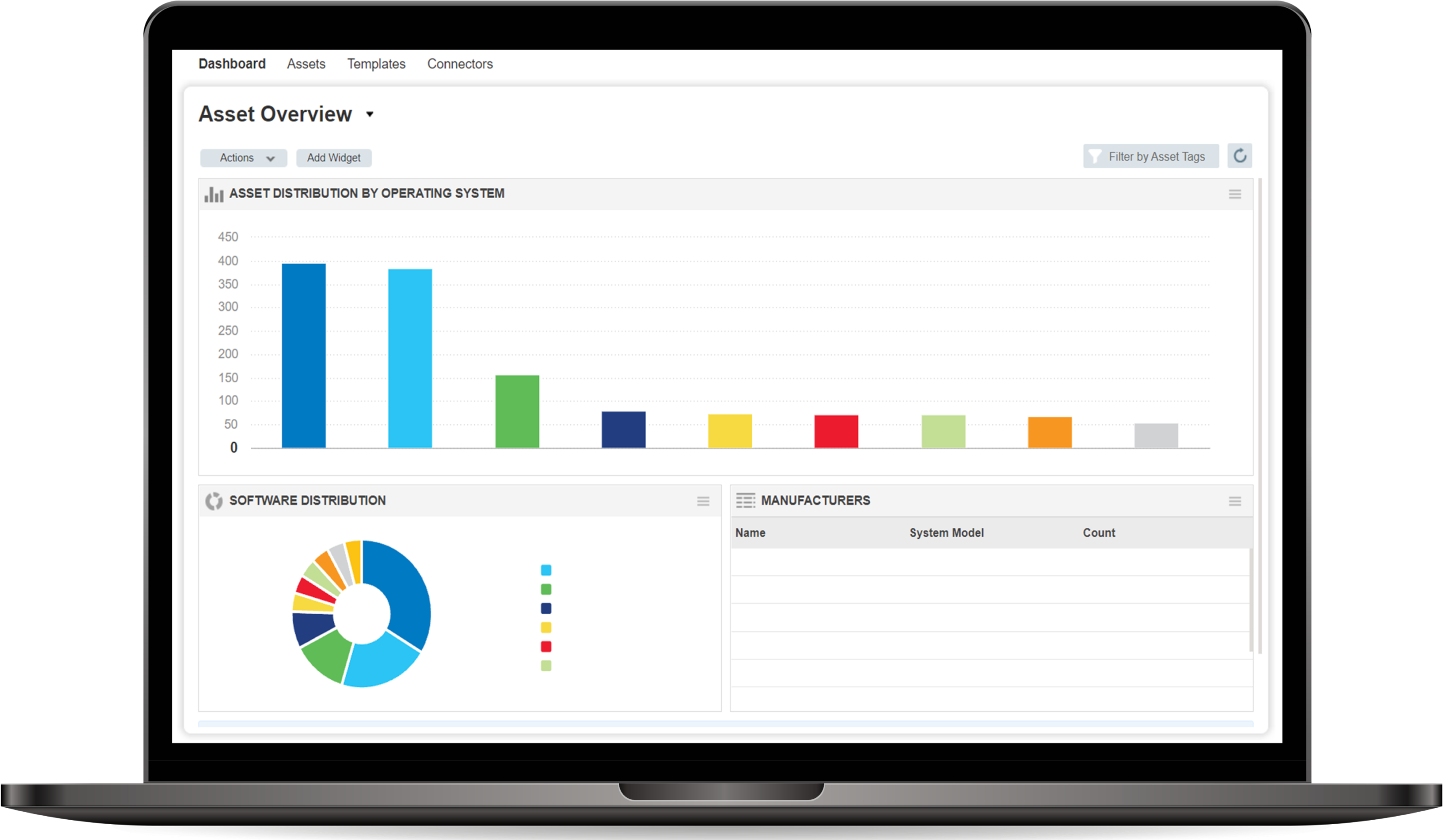
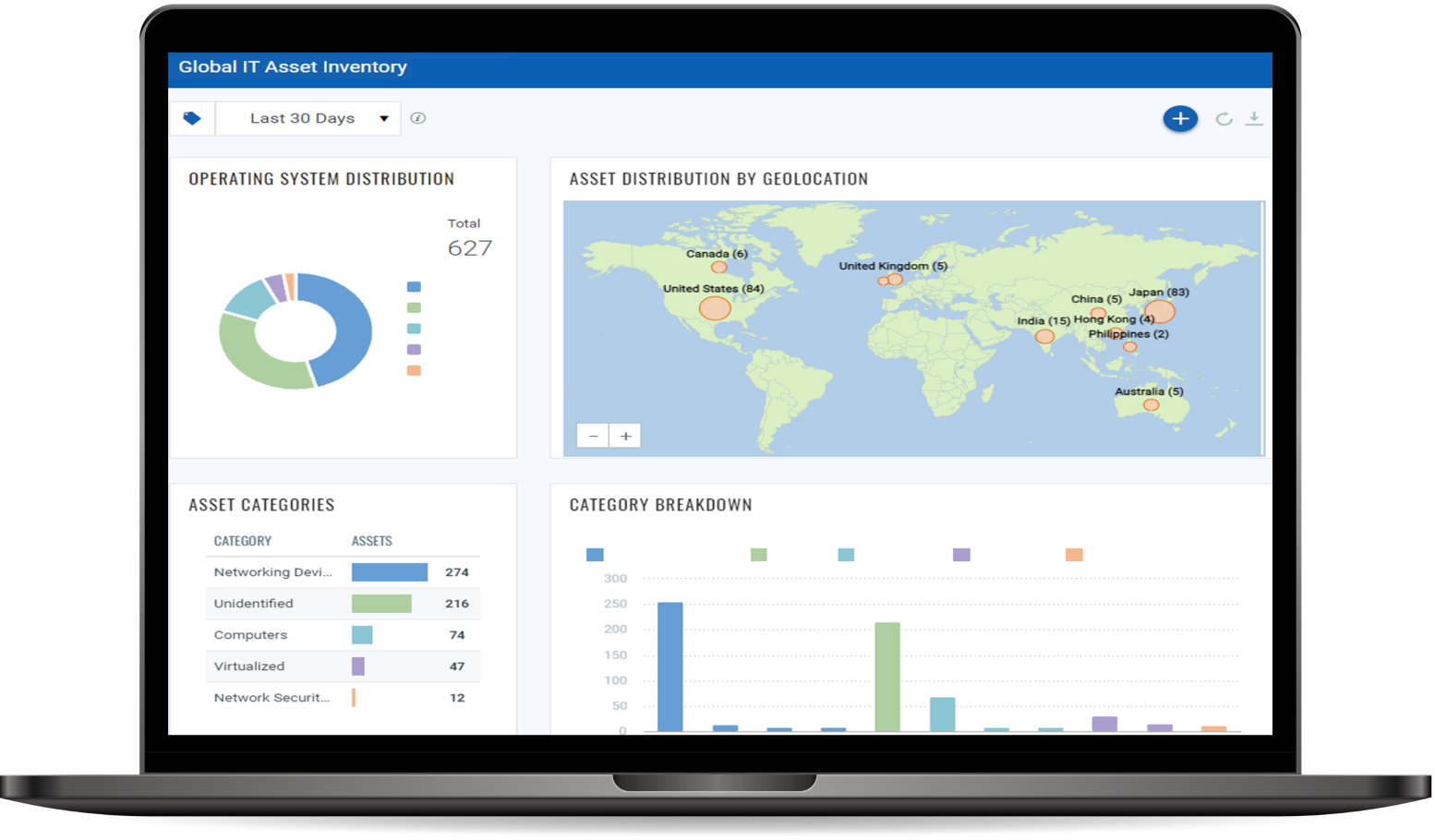
IT Asset Discovery
Automatically identify all known and unknown assets in your global hybrid-IT with complete visibility of on-premises devices and applications, endpoints, clouds, containers, mobile, OT, and IoT. From there, you’ll have a comprehensive, categorized inventory enriched with details like vendor lifecycle information.
IT Asset Management
Automated normalization and classification of asset data streamline your IT asset management and integration into various IT processes like change management, patching, and incident response. A continually updated asset database transforms your global IT asset inventory into structured, multidimensional information. This allows for more informed business decision-making.
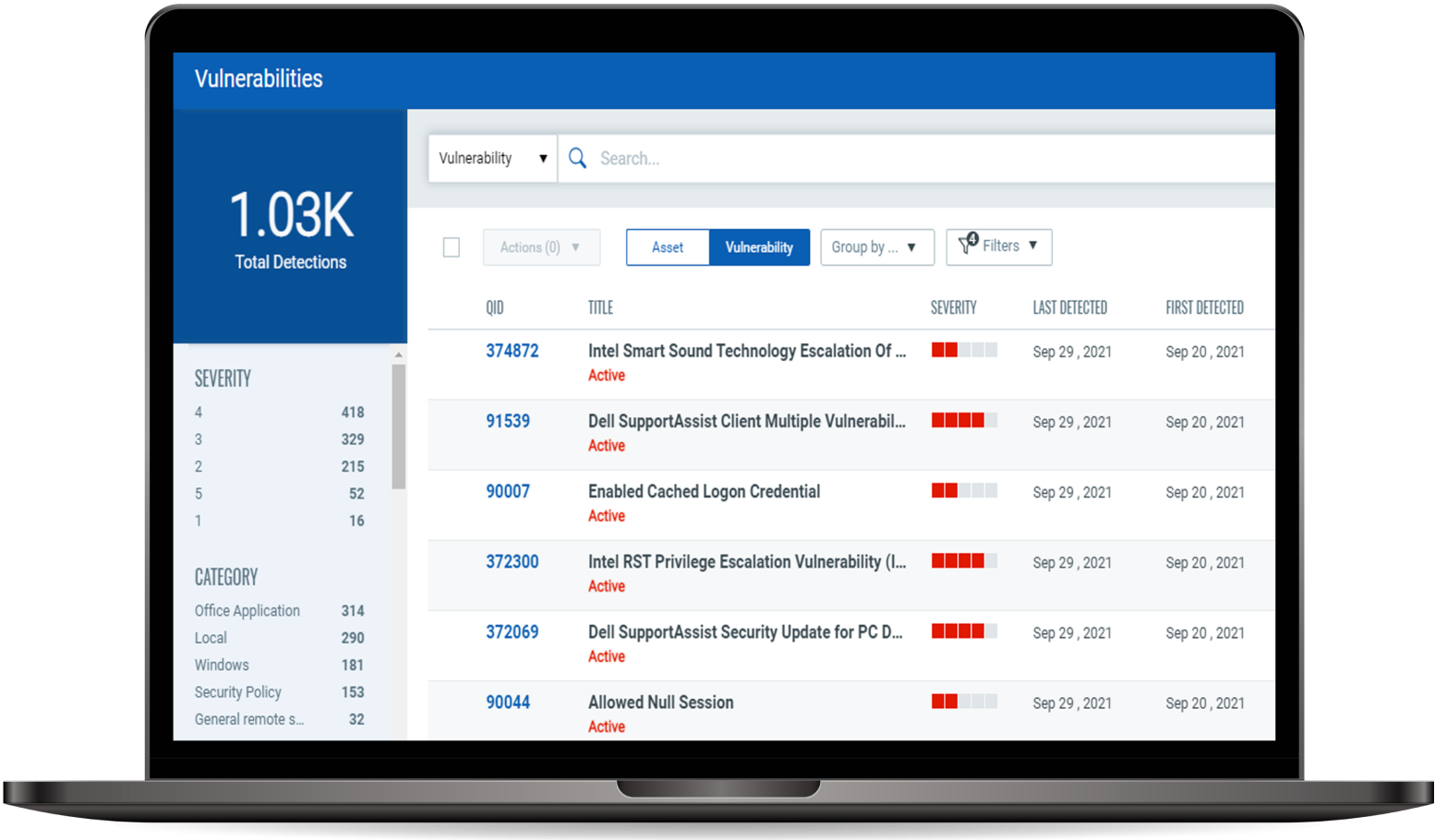
Vulnerability Scanning
Breaches usually exploit known bugs. Removing these vulnerabilities is crucial to protect sensitive information. Our vulnerability scanning services can help automatically identify weaknesses, assign tickets for remediation, manage exceptions, and list patches for each host. Next, they’ll auto-generate reports for different stakeholders, such as executives, IT managers, or auditors.
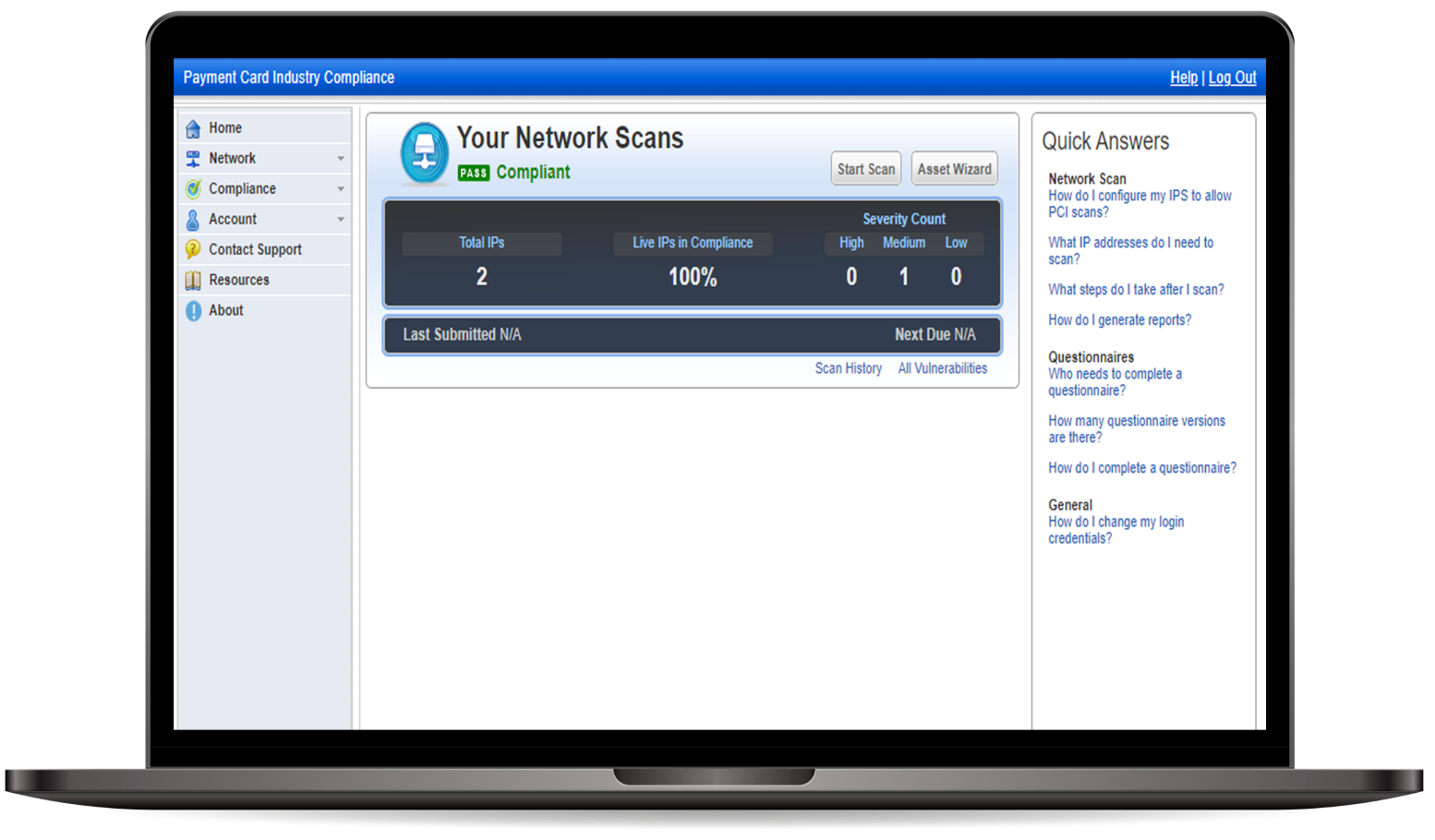
PCI ASV Scanning
Achieve PCI DSS compliance and ensure network security with our managed PCI ASV Scanning services. Our cloud-based solution streamlines the process and provides a proof of compliance.
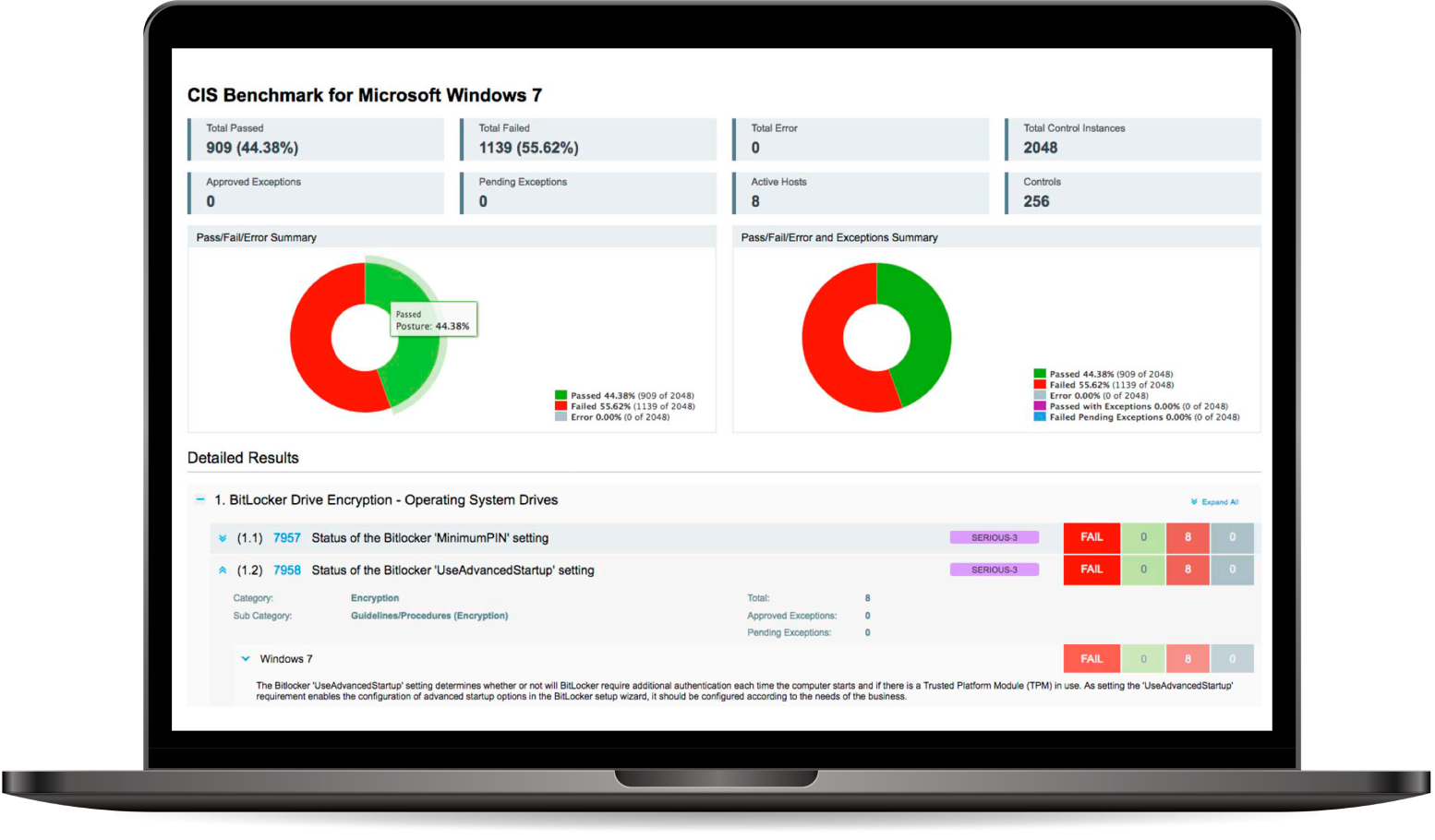
Security Configuration / CIS Benchmarks Audit
To ensure a complete vulnerability management program, it’s vital to perform configuration assessments. Our Security Configuration compliance services help you identify security weaknesses and assess your compliance with industry standards like vendor security best practices, CIS Benchmarks, COBIT, ISO, NIST SP800-53, HIPAA, FFIEC, and NERC-CIP.
Cloud Security Assessment
Make sure your cloud assets and resources are secure with our cloud security assessment services. We’ll identify and address potential security threats, such as misconfigurations, unauthorized access, and non-standard deployments. Our automated security monitoring is based on industry standards and regulations, protecting against issues like leaky storage buckets, unrestricted security groups, and crypto-mining attacks across major cloud providers like AWS, Azure, and Google..
Container Security
With PurpleBox Vulnerability Management, get a complete, comprehensive view of security for your containerized environments. Scan your container images, container hosts, and containers during runtime. Integrate with your DevOps and CI/CD processes to easily identify risks and catch drift from your approved images, all in real-time.
Benefits of Vulnerability Management
Adopt Transparency
With real-time alerts and notifications, you can be proactive in addressing possible risks as soon as new vulnerabilities emerge. Identify vulnerabilities, prioritize remediation, and assess IT compliance while having total and complete visibility into your data center assets.
Shadow IT
Identify and organize your host assets by discovering forgotten devices. You can rapidly determine what's actually running within various regions of your network, from your perimeter and corporate network to virtualized machines and cloud services like Amazon EC2.
Scan for vulnerabilities
Scan multiple systems from a single console, including your perimeter, internal network, and cloud environments (such as Amazon EC2). Since scanning and reporting are separated in our working method, you may scan in-depth and then develop unique reports that show each audience the exact detail level.
Customize reports
Use interactive reports to better understand your network's security through the vulnerability data collected across hosts. Change what's presented or choose other groupings of assets without the trouble of rescanning by using a library of built-in reports. Reports can be prepared on-demand or automatically., whenever you want, without having to rescan.
Remediate vulnerabilities
Keep track of how each vulnerability within each host is handled over time. This allows you to keep track of the actions you took in response to each vulnerability and assess how effective your remediation efforts were, allowing you to.
Prioritize and identify threats
You may use trend analysis, Zero-Day, and Patch impact estimates to determine the highest business risks using Qualys. Instead of taking single snapshots, examine your network's vulnerabilities over time and at various degrees of detail.
Why PurpleBox Security?
PurpleBox Security specializes in Security assessment and Pentesting services. We place a high value on testing important devices and components. Our comprehensive reports are produced by experienced, skilled testers so that the actionable information contained within them is easily understood. Combining our Red Team (Offensive) capabilities with our Blue Team (Defensive) experience, we provide a unique approach to solving enterprise security problems.
What is Apache Log4J Vulnerability and How to Prevent It?
December 17, 2021
Qualys PM and EDR Remediation Demonstration
September 15, 2021
Overcome Your SecurityChallenges
We offer 360° Security protection for your business with our trusted experts in cybersecurity.