February 2, 2023
What is Red Teaming?
January 17, 2023
Linux Privilege Escalation with PATH Variable & SUID Bit
July 20, 2022
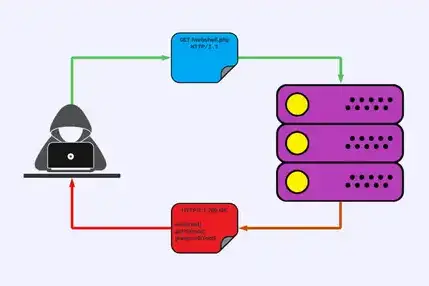
Methods For Exploiting File Upload Vulnerabilities
April 25, 2022
10 GitHub Security Best Practices
April 13, 2022
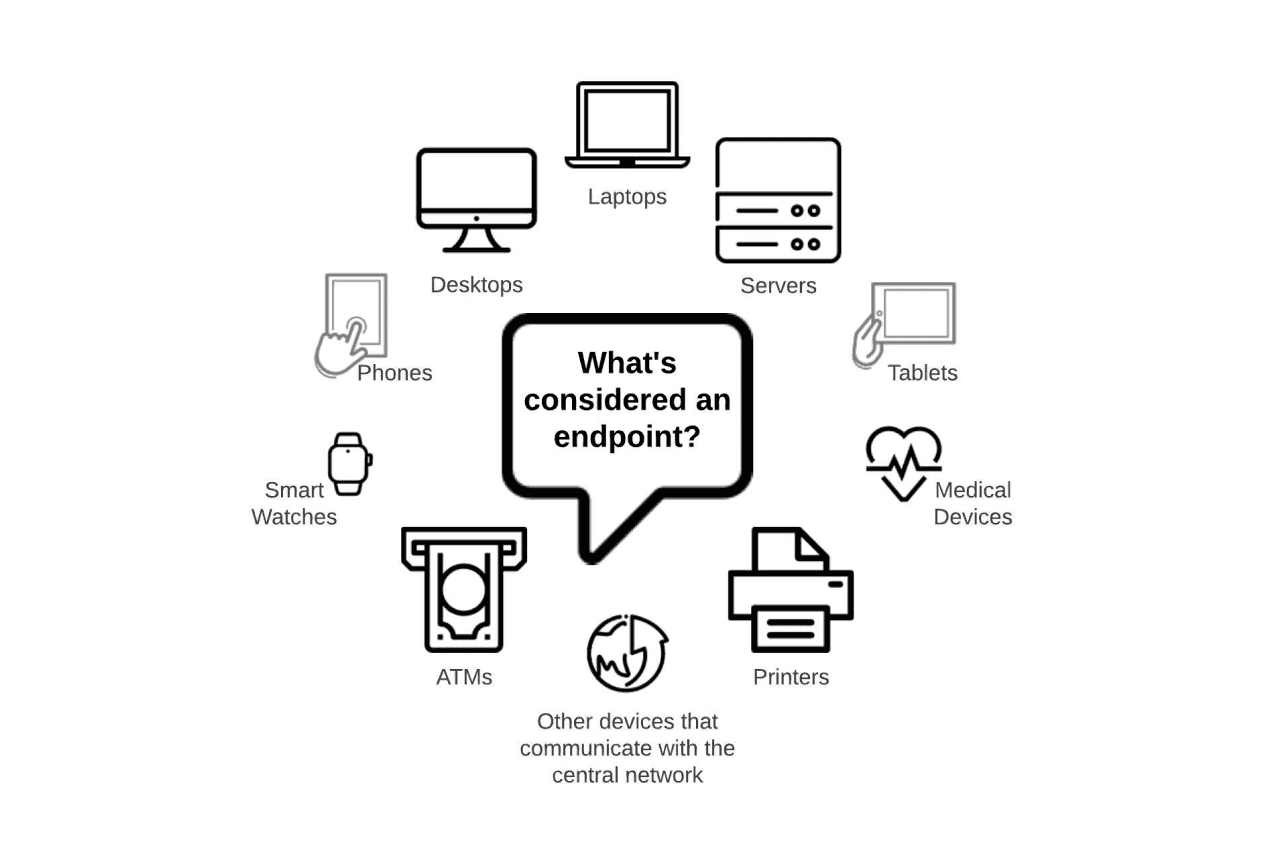
What is Endpoint Security?
January 19, 2022
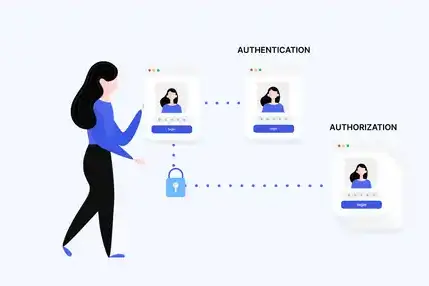
Broken Access Control vs Broken Authentication
September 29, 2021